- This week was saudi and oman national ctf by cyber talents. The capture the flag had lesser number of challenge selection. It was fun!
Web Category: backtoBasics
-
Question: —> Easy —> not pretty much many options. No need to open a link from a browser, there is always a different way
-
Thoughts: Used
telnet, curl, httpie, ssl, opensslways to connect to the url with no luck.
# HEAD request
$ curl -I http://35.197.254.240/backtobasics/
HTTP/1.1 200 OK
Server: nginx/1.10.3 (Ubuntu)
Date: Fri, 08 Feb 2019 22:55:57 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
Allow: GET, POST, HEAD,OPTIONS
# POST request
$ curl -d '{"key1":"value1", "key2":"value2"}' -H "Content-Type: application/json" -X POST http://35.197.254.240/backtobasics/
<!--
var _0x7f88=["","join","reverse","split","log","ceab068d9522dc567177de8009f323b2"];function reverse(_0xa6e5x2){flag= _0xa6e5x2[_0x7f88[3]](_0x7f88[0])[_0x7f88[2]]()[_0x7f88[1]](_0x7f88[0])}console[_0x7f88[4]]= reverse;console[_0x7f88[4]](_0x7f88[5])
-->$
# GET request - obviously when executed from a browser this would redirect to google.com
$ curl -g http://35.197.254.240/backtobasics/
<script> document.location = "http://www.google.com"; </script>srimbp:dev sri$
# Also tried with /backtobasics in vain for a long time until changed to `/backtobasics/`
Steps:
- POST request works
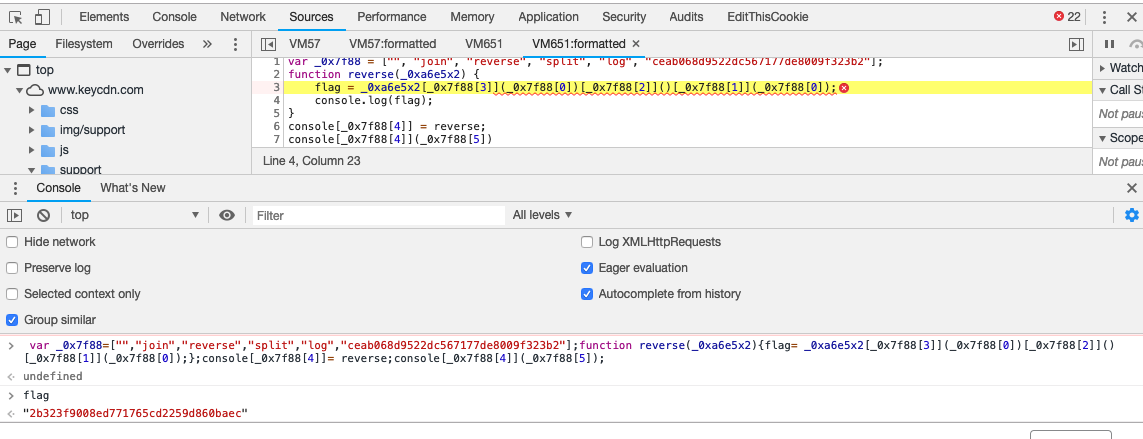
- As already shown above, POST method worked and returned a javascript which when run in console had set the flag in the variable
flag
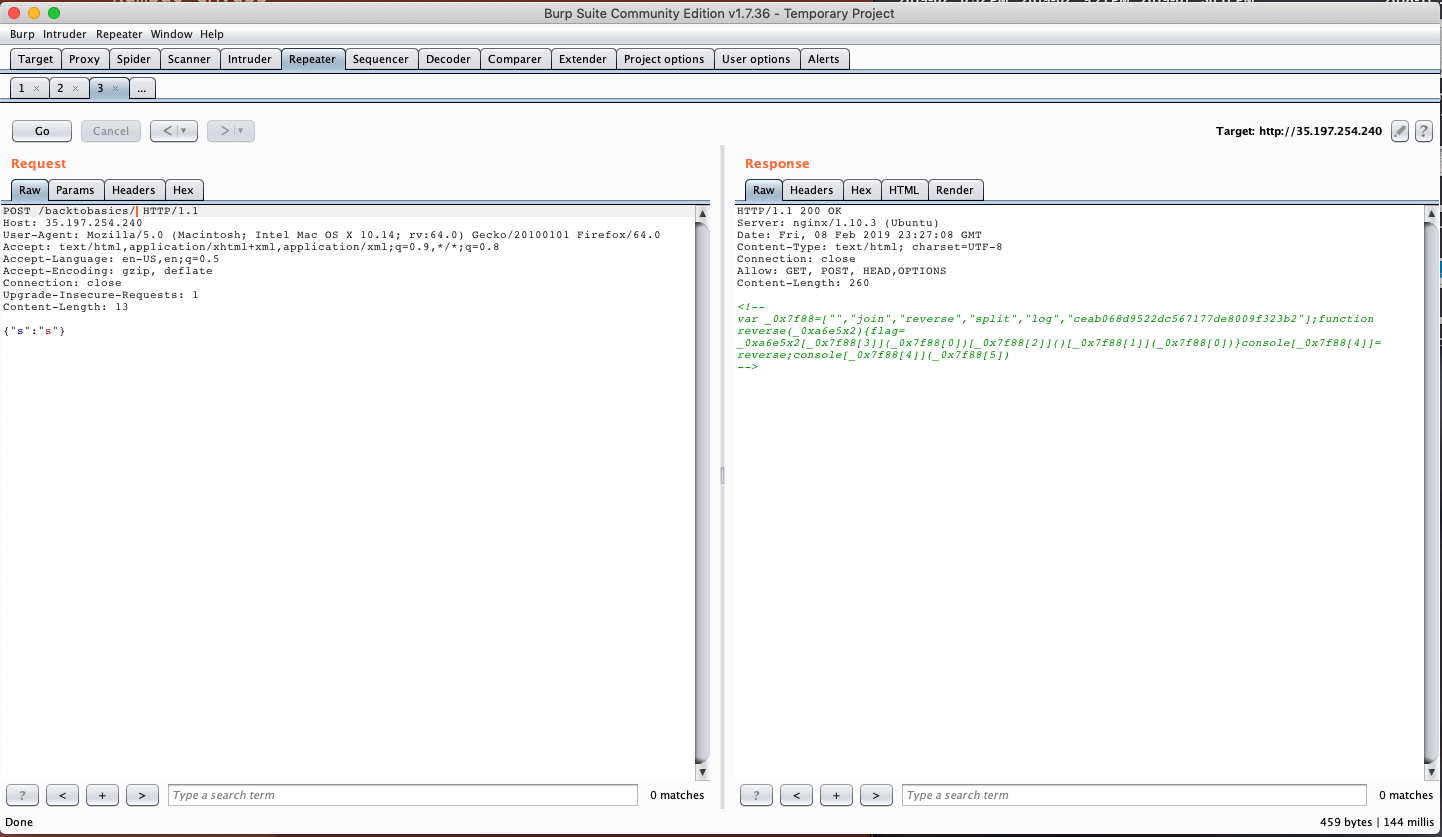
Output:
Flag:2b323f9008ed771765cd2259d860baec
Other Tries:
- Telnet
```bash
telnet 35.197.254.240 80
Trying 35.197.254.240…
Connected to 240.254.197.35.bc.googleusercontent.com.
Escape character is ‘^]’.
POST backtobasics/
HTTP/1.1 400 Bad Request
Server: nginx/1.10.3 (Ubuntu)
Date: Fri, 08 Feb 2019 23:17:05 GMT
Content-Type: text/html
Content-Length: 182
Connection: close
Allow: GET, POST, HEAD,OPTIONS
400 Bad Request
Connection closed by foreign host.
srimbp:dev sri$ telnet 35.197.254.240 80
Trying 35.197.254.240…
Connected to 240.254.197.35.bc.googleusercontent.com.
Escape character is ‘^]’.
POST /backtobasics/
400 Bad Request
Connection closed by foreign host.
srimbp:dev sri$
- Openssl
srimbp:dev sri$ openssl s_client -connect 35.197.254.240:80
CONNECTED(00000003)
4560729708:error:1400410B:SSL routines:CONNECT_CR_SRVR_HELLO:wrong version number:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22.240.1/libressl-2.6/ssl/ssl_pkt.c:386:
—
no peer certificate available
—
No client certificate CA names sent
—
SSL handshake has read 5 bytes and written 0 bytes
—
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : 0000
Session-ID:
Session-ID-ctx:
Master-Key:
Start Time: 1549666111
Timeout : 7200 (sec)
Verify return code: 0 (ok)
—
```
Forensics Category: Godot
- Level: Easy
Given
- A image (png)
- Specific question: an hacker has left some info in the png that helps us to track him.
Thinking…
- Used pnginfo, exifinfo, exif, imginfo, cat image, bin walk (got carried away with the lib file initially)
- Most of the information reveal about a png tailer
- Visually you can see a base64 type string at the end too
- Decoding base64 we get a hex.
- Try all the tracking possibilities —> latitude + longitude or ip ?
- Then… after some break –> rethinking this to be an easy problem
- Tried Base32 decode and the Flag was revealed
Steps
- Visually in a vi editor the tailer of the image is visible else any image info tool would have revealed about a tailer
- Looking at the magic number number for trailer of png images you can separate the data from the png image.
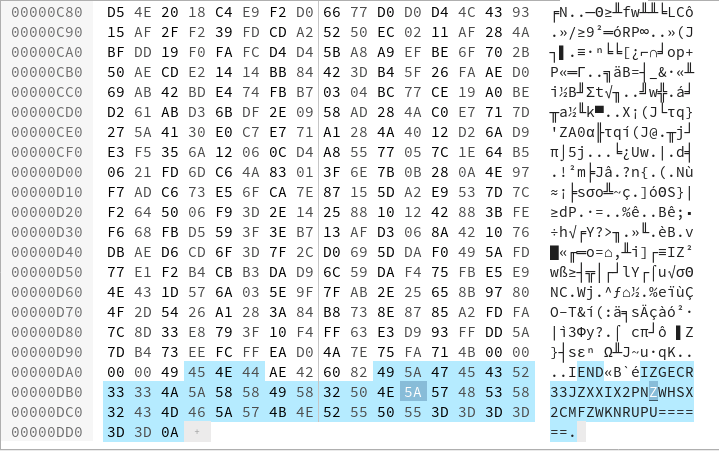
Flag
- FLAG{Not_Only_Base64}
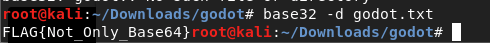
Console
Proper calc steps
root@kali:~/Downloads/godot# file godot.png
godot.png: PNG image data, 64 x 64, 8-bit/color RGBA, non-interlaced
root@kali:~/Downloads/godot# pngcheck godot.png
godot.png additional data after IEND chunk
ERROR: godot.png
root@kali:~/Downloads/godot# exiftool godot.png
ExifTool Version Number : 11.16
File Name : godot.png
Directory : .
File Size : 3.5 kB
File Modification Date/Time : 2019:02:09 01:41:06-08:00
File Access Date/Time : 2019:02:09 01:41:17-08:00
File Inode Change Date/Time : 2019:02:09 01:41:06-08:00
File Permissions : rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 64
Image Height : 64
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Warning : [minor] Trailer data after PNG IEND chunk
Image Size : 64x64
Megapixels : 0.004
Results:
root@kali:~/Downloads/godot# python
>>> import base64
>>> base64.b64decode("91841df795d78f59587I820VVd4T=")
'\xf7_8\xd5\xd7\xfb\xf7\x97{\xf1\xfe}\xe7\xce\xc8\xf3m\x15U\xde\x13'
root@kali:~/Downloads/godot# base32 -d godot.txt
FLAG{Not_Only_Base64
Overthinking…
root@kali:~/Downloads/godot# steghide extract -sf godot.png
root@kali:~/Downloads/godot# binwalk godot.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 64 x 64, 8-bit/color RGBA, non-interlaced
41 0x29 Zlib compressed data, default compression
root@kali:~/Downloads/godot# img_stat godot.png
IMAGE FILE INFORMATION
--------------------------------------------
Image Type: raw
Size in bytes: 3539
Sector size: 512
>>> import zlib
>>> h = open("29.zlib","r")
>>> data = h.read()
>>> zlib.decompress(data)
Forensics Category: info
Given
info.jpg- image file with some hidden information- Difficulty: Medium
Thinking…
- As usual, check the image information in all the tools
- exiftool
- img_stat
- file
- binwalk
- exif
- Just view file in hex editor or just as easy as cat
- Everything seemed usual except for the comment
badisbad - Using
steghideto extact files with the comment as the passphrase is a success.. - (solved this after the ctf end).. Got pulled into jsteg and into another approach as a detour!
Steps:
- Look at the image information
- Collect unusual or user entered info like comments, trailer or headers
- Use steghide to extract with known string as password
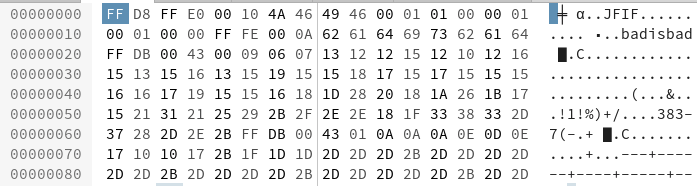
- complete steps

Flag
flag{Stegn0_1s_n!ce}
Other attempts:
root@kali:~/Downloads/info# cat extract.go
package main
import (
"fmt"
"os"
"github.com/lukechampine/jsteg"
)
func main() {
f, _ := os.Open("info.jpg")
hidden, _ := jsteg.Reveal(f)
fmt.Println(hidden)
}
root@kali:~/Downloads/info# go run extract.go
[0 32 34 162 80 44 102 15 1 109 232 66 0 2 64 12 10 151 96 62 2 34 129 240 166 241 214 198 136 156 1 32 235 171 4 48 5 128 131 206 152 73 116 16 53 34 133 53 9 4 33 1 232 196 160 68 58 108 16 131 2 44 1 181 132 48 0 23 84 5 90 160 131 47 40 16 40 0 9 48 240 112 128 104 148 33 117 0 38 144 82 130 8 44 36 182 131 60 4 3 176 168 112 24 2 243 129 17 188 96 21 68 62 96 52 1 106 144 216 0 82 7 13 65 80 0 125 72 56 136 29 80 97 84 64 65 136 50 49 165 185 124 82 132 59 133 76 27 32 28 210 253 138 110 2 13 64 136 144 192 161 193 27 219 192 51 34 230 218 8 101 3 3 131 242 8 128 82 52 7 164 141 226 196 35 28 37 0 16 104 10 181 225 10 18 97 4 160 97 16 138 2 140 113 2 11 171 176 12 154 80 17 110 84 123 116 147 33 34 182 146 0 214 92 99 89 83 34 136 90 219 133 37 4 6 143 98 26 146 44 6 202 137 217 165 233 39 250 33 160 65 178 69 108 254 12 186 14 102 17 19 12 215 184 1 188 81 32 37 205 200 72 147 6 225 88 209 67 72 89 2 72 184 26 0 160 18 208 16 164 223 0 113 201 81 34 19 68 54 211 35 9 118 88 66 76 18 1 84 56 65 192 4 2 129 165 6]
Misc Category: Just another conference
- popular conference organized by owasp ==>
AppSec
