NeverLan Ctf 2019
- NeverLan is mostly a middle school ctf but everyone are welcome to participate and have fun! Let the fun begin…
-
This also provides a motivation to start ctfing…
- I got pictures of some challenges while some asset remain unupdated!
Categories
Scripting/Coding
- webCipher
- Easy Caesar Shift Cipher
Code:
import sys
import urllib2
cipherText = list("jllnunajcxa")
for i in range(0, 26):
#print "Caesar Shift: " + str(i)
plainText = ""
for j in range(len(cipherText)):
caesar_plain = ord(cipherText[j])+i
#print caesar_plain, cipherText[j]
if caesar_plain > 122:
caesar_plain = caesar_plain - 122
while (caesar_plain - 122) > 122:
caesar_plain = caesar_plain - 122
caesar_plain = 96 + caesar_plain
plainText += chr(caesar_plain)
print "Requesting with caesar shift " + str(i) + ", plaintext: " + plainText
request = urllib2.urlopen("https://challenges.neverlanctf.com:1160/?deciphered="+plainText)
response = request.read()
if "flag" in response:
print response
sys.exit()
Output:
srimbp:neverLanCtf sri$ python caesarCipher.py
Requesting with caesar shift 0, plaintext: jllnunajcxa
Requesting with caesar shift 1, plaintext: kmmovobkdyb
Requesting with caesar shift 2, plaintext: lnnpwpclezc
Requesting with caesar shift 3, plaintext: mooqxqdmfad
Requesting with caesar shift 4, plaintext: nppryrengbe
Requesting with caesar shift 5, plaintext: oqqszsfohcf
Requesting with caesar shift 6, plaintext: prrtatgpidg
Requesting with caesar shift 7, plaintext: qssubuhqjeh
Requesting with caesar shift 8, plaintext: rttvcvirkfi
Requesting with caesar shift 9, plaintext: suuwdwjslgj
Requesting with caesar shift 10, plaintext: tvvxexktmhk
Requesting with caesar shift 11, plaintext: uwwyfylunil
Requesting with caesar shift 12, plaintext: vxxzgzmvojm
Requesting with caesar shift 13, plaintext: wyyahanwpkn
Requesting with caesar shift 14, plaintext: xzzbiboxqlo
Requesting with caesar shift 15, plaintext: yaacjcpyrmp
Requesting with caesar shift 16, plaintext: zbbdkdqzsnq
Requesting with caesar shift 17, plaintext: accelerator
<!DOCTYPE html>
<html>
<head>
<title>anti-human cipher</title>
</head>
<body>
<div id="key">
<h1>You got it!<h1>
<p>flag{H3llo_c4es3r}</p>
</div>
</body>
</html>
Trivia
- The oldest SQL Injection Vulnerability. The flag is the vulnerability ID?
- Ans:
CVE-2000-1233 - Note:
- Fetch the CVE list for sqli and navigate to the end.
- Ans:
- In MSSQL Injection Whats the query to see what version it is?
- Ans:
SELECT @@version
- Ans:
- A domain-specific language used in programming and designed for managing data held in a relational database management system, or for stream processing in a relational data stream management system?
- Ans:
SQL
- Ans:
- A group of similar binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation?
- Ans:
base64
- Ans:
- A small piece of data sent from a website and stored on the user’s computer by the user’s web browser while the user is browsing?
- Ans:
cookie
- Ans:
- A standard used by websites to communicate with web crawlers and other web robots. The standard specifies how to inform the web robot about which areas of the website should not be processed or scanned?
- Ans:
Robots Exclusion Standard
- Ans:
- Why make bacon when you can make a cipher instead?
If only I could remember what it’s called…- Ans: ``
- Notes:
- Notes: I did not solve this, I read a lot about baconian cipher in wiki and tried different strings, but nothing was accepted. Hope it is Bacon’s Cipher or Baconian https://puzzling.stackexchange.com/questions/8143/one-word-bacon
- A command line tool that tells you whois hosting a particular website?
- Ans:
whois
- Ans:
- What is the common name for a single element of Amazon Simple Storage Service?
- Ans:
S3 Bucket
- Ans:
- When hosting a site as an S3 bucket, the bucket name must __ the domain name.
- Ans:
Match
- Ans:
- What type of namespace prevents two AWS S3 buckets having the same name?
- Ans:
global
- Ans:
- What does AWS stand for?
- Ans:
Amazon Web Services
- Ans:
- what does sudo stand for?
- Ans:
Super User Do
- Ans:
- What are the policies called that you use to grant access to your AWS S3 buckets and objects to the general public?
- Ans:
ACL(I was trying with access control list and other policy names in AWS S3 for allowbucketpublic stuff)
- Ans:
- What is $PATH on linux?
- Ans:
Environmental Variable - Note:
- I knew it represents the path but wanted the answer to be brief so tried a simplet env and that was the answer.
- Ans:
- When bash is invoked as an interactive login shell it first reads and executes commands from this file.
- Ans:
bash_profile
- Ans:
- When bash is invoked as an interactive non-login shell it first reads and executes commands from this file
- Ans:
bashrc
- Ans:
Recon
- occurring in Chicago, Illinois, United States, on the evening of November 22. There was an interruption like nothing we had ever seen before.
What was the name of the Intruder?- Ans:
Max Headroom(wiki about events on that data and search for chicago)
- Ans:
- I love Github. Use it all the time! Just wish they could host a webpage…
- Ans:
flag{Th1s_g1thub_l00ks_a_l1l_sparc3} - Notes:
- Assumed it should be githubPages or username.github.io or even thought it should be (assuming title of this challenge purvesta being a hint) –> purvesta.github.io and then found the flag in the repo as lol..
- Ans:
- Back in the day, Zesty hid a flag in the first version of our website.
- Ans: ``
- This organizations creation was announced Mon Sep 24 2001. What is the full name of the organization?
- Ans:
Open Web Application Security Project
- Ans:
-
It looks like N30 has been keeping passwords secret with some software he wrote, but he should know better than to rely on proprietary software for security. It looks like he left the repo public too!
- Ans:
root@kali:~/Desktop/KeyZ# ./key -n passwords.keyz
32 64 331
root@kali:~/Desktop/KeyZ# ./key -g passwords.keyz
ERROR(key): no key was specified for key file 'passwords.keyz'
root@kali:~/Desktop/KeyZ# ./key -d passwords.keyz
DEBUG(key): opening passwords.keyz for reading
DEBUG(key): magic bits are: KEYZ
root@kali:~/Desktop/KeyZ# ./key -n passwords.keyz
32 64 331
root@kali:~/Desktop/KeyZ# ls
HOWTO.md key.cpp key.o makefile README.md smaz.h smaz.o
key key-man.txt LICENSE passwords.keyz smaz.cpp smaz-LICENSE
root@kali:~/Desktop/KeyZ# ./key -g passwords.keyz
ERROR(key): no key was specified for key file 'passwords.keyz'
root@kali:~/Desktop/KeyZ# ./key -g passwords.keyz flag
flag{bu7_1ts_pr0pr1etary}
�Proot@kali:~/Desktop/KeyZ#
Notes:
* Unrelated research
- Mobef ransomware trojan
- Encrypts all the sensitive info files (predefined file extensions) with RSA 2048 AES CBC
- Reference: https://malwaretips.com/blogs/remove-mobef-virus/
- Changes wallpaper into a ransom note
- Delievered by:
* Email
* So, Mobef ransomware encrypted file...Decrypt it?
* neverLan website --> Creators --> N30 (Given in the problem) --> Track N30 in twitter (as no github was given) --> Get real name --> Search + Goto Github account --> Owner of neverLanCtf so we are on right path --> Keyz project --> Make project --> Read readme --> Operating with --n worked giving some values --> It stores key value pairs so we want flag --> get flag
Web
- React to this… It looks like someone set up their react site wrong…
- Ans: The source files had an admin page in react structure which consisted the flag.
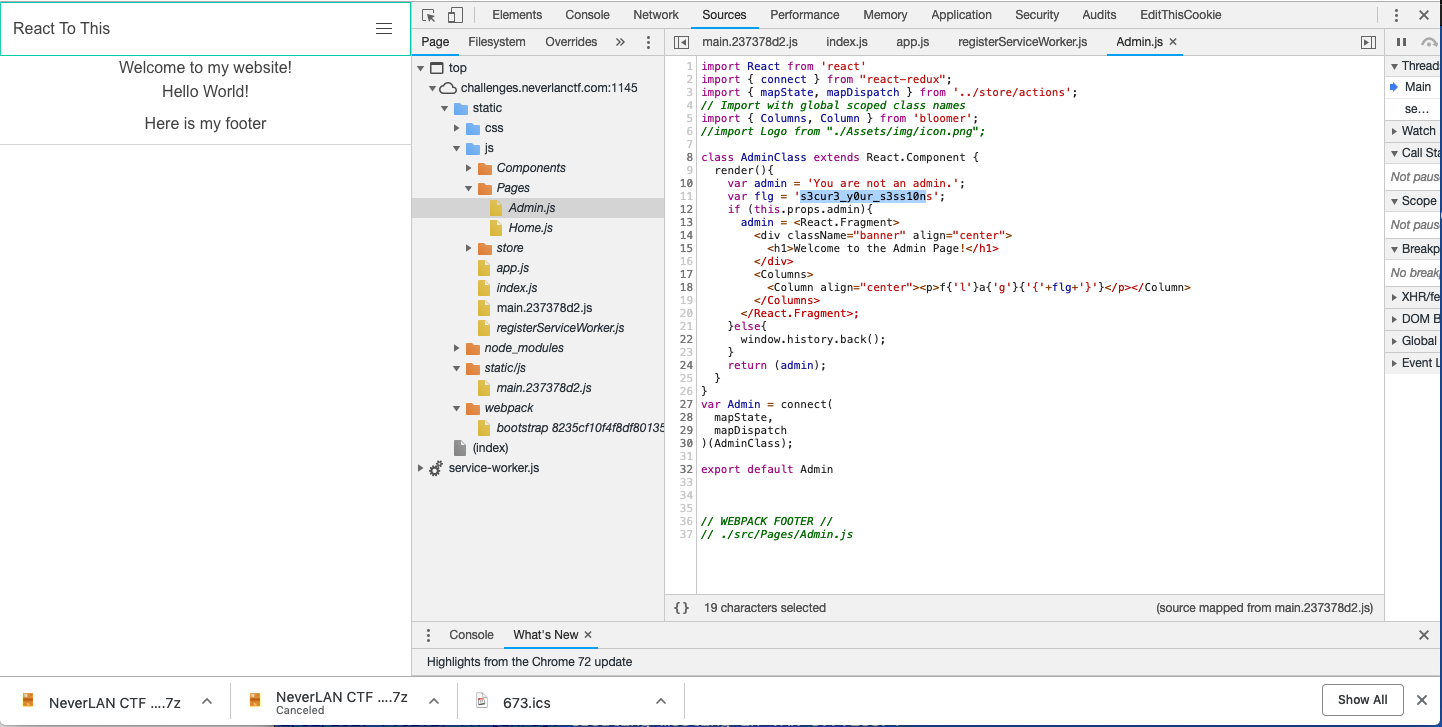
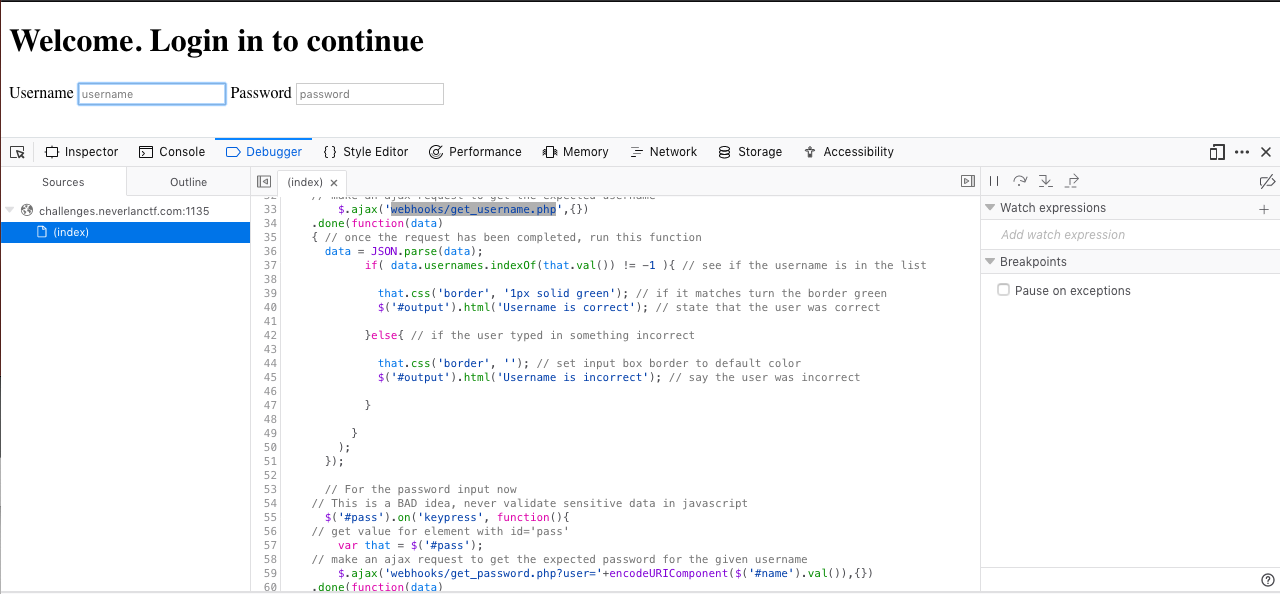
- Dirty validation… To keep my server from doing a lot of work, I made javascript do the heavy lifting of checking a user’s password
- Ans: get_username.php and get_password.php is called internally, executing them (HTTP requests) provides usernames and corresponding password which can then be used to login and get the flag.
More at Assets
- SQL Fun 1 - EPORT: ‘My Customer forgot his
Password. HisFnameis Jimmy. Can you get his password for me? It should be in theuserstable’- Ans: select * from users where fname=”Jimmy”;
flag{SQL_F0r_Th3_W1n}
- Ans: select * from users where fname=”Jimmy”;
- SQL Fun 2 - REPORT: A Client forgot his Password… again. Could you get it for me? He has a users account and his Lname is Miller if that helps at all. Oh! and Ken was saying something about a new table called passwd; said it was better to separate things
- Ans: select * from users left join passwd where users.Lname = “Miller”; and then base64 decode… flag{W1ll_Y0u_J01N_M3?}
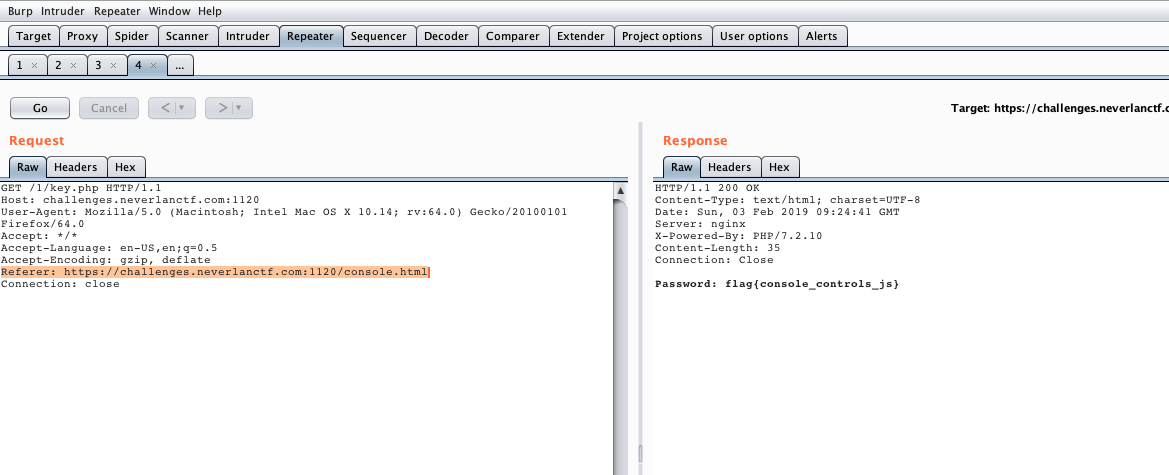
- Console - You control the browser
- Ans: Password: flag{console_controls_js}
- Notes:
* There was a client side hash check
- Initially tried hashkiller, hashcat, bruteforcing the hash but it was meaning less as the password was not used anywhere else
- Tried to make request to key.php - the target asset by exeucting js function, forged requests and separate ajax requests to match the headers. Also tried all http methods to receive 405s
- The js and submit event did not line up... were way off..
- The form action was intriguing, trying that made success. But the answer was just the existence of referer header in the request.
* If you can't find it you're not looking hard enough - if you can't find it you're not looking hard enough
Ans: This was a trick where you might tend to overthink but for this challenge looking at the source code had the flag hardcoded...flag{Whale_w0u1d_y0u_l00k3y_th3r3}
Crypto
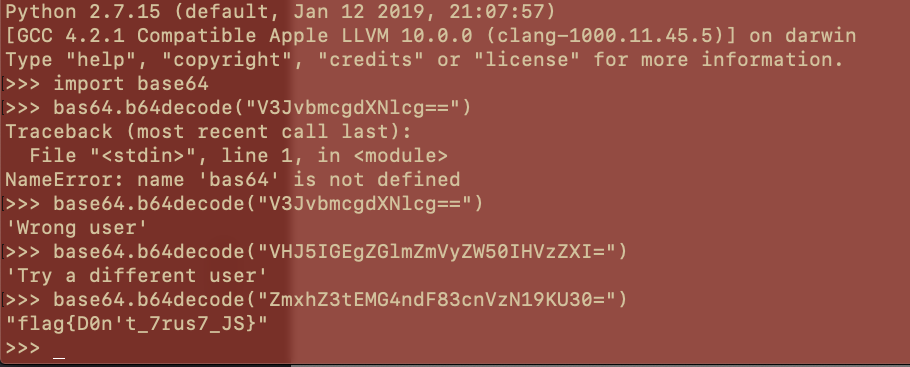
- Cover the BASEs
- A very easy challenge, just base64 decode
>>> import base64 >>> base64.b64decode("ZmxhZ3tEMWRfeTB1X2QwX3RoM19QcjNfQ1RGfQ==") 'flag{D1d_y0u_d0_th3_Pr3_CTF}'
- A very easy challenge, just base64 decode
- Alphabet Soup
-
Ciphertext:
MKXU IDKMI DM BDASKMI NLU XCPJNDICFQ! K VDMGUC KW PDT GKG NLKB HP LFMG DC TBUG PDTC CUBDTCXUB. K’Q BTCU MDV PDT VFMN F WAFI BD LUCU KN KB WAFI GDKMINLKBHPLFMGKBQDCUWTMNLFMFMDMAKMUNDDA
- Ans:
- Automation??
- Using online tool at https://www.guballa.de/substitution-solver
- NICE GOING ON SOLVING THE CRYPTOGRAM! I WONDER IF YOU DID THIS BY HAND OR USED YOUR RESOURCES. I’M SURE NOW YOU WANT A FLAG SO HERE IT IS FLAG DOINGTHISBYHANDISMOREFUNTHANANONLINETOOL
- Notes:
- Alphabet mapping to different characters within alphabet list
- Tried
Caesar method or ROTof shifting but all the mapping is not uniform so Caesar method might not work… Substitution Cipher! Mono? or Poly?probably Poly- Reason: One particular manual finding is
K'Q–>I'D, which matches all the existence ofK–>Ibut Q vs D mapping is way off so no uniformity… - Different way to automate or manual way?
-
- OldSchool Crypto
- Ciphertext Recon:
- Looks like mobile towers in phone and greater than symbols
- Ans:
yourflagissomanycryptos - Notes:
* Look at ancient ciphers - Greek ciphers - Wakanda scripts - Eqypt ciphers - Pigeon ciphers * Google reverse image search was not successfull, resulted in multiple black backgrounds * Rechecking across different types of ancient scripts/ciphers did not help much. * Finally, cropping a part of the image, just one cipher and performing reverse search --> https://fr.wikipedia.org/wiki/Num%C3%A9ration_m%C3%A9sopotamienne --> https://en.wikipedia.org/wiki/Babylonian_numerals * So, babylion numerals it is --> 25 15 21 18 + 6 12 1 7 + 9 19 + 19 15 + 13 1 14 + 25 3 18 25 16 20 15 19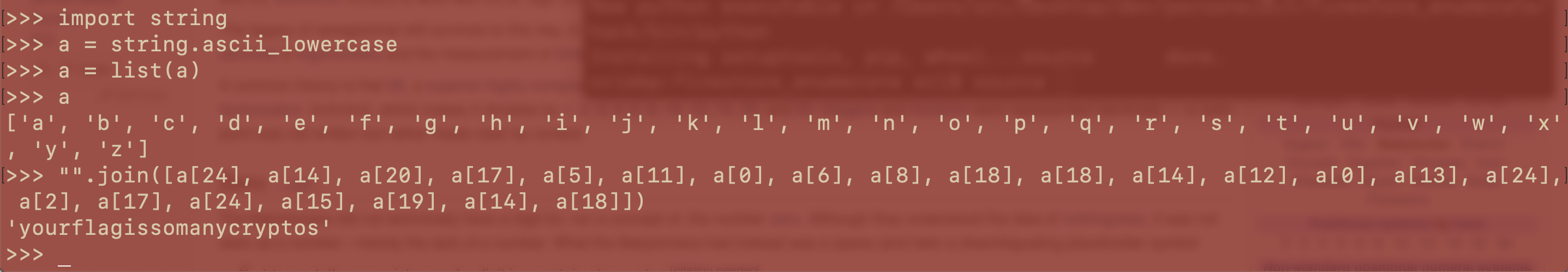
- Ciphertext Recon:
Cloud
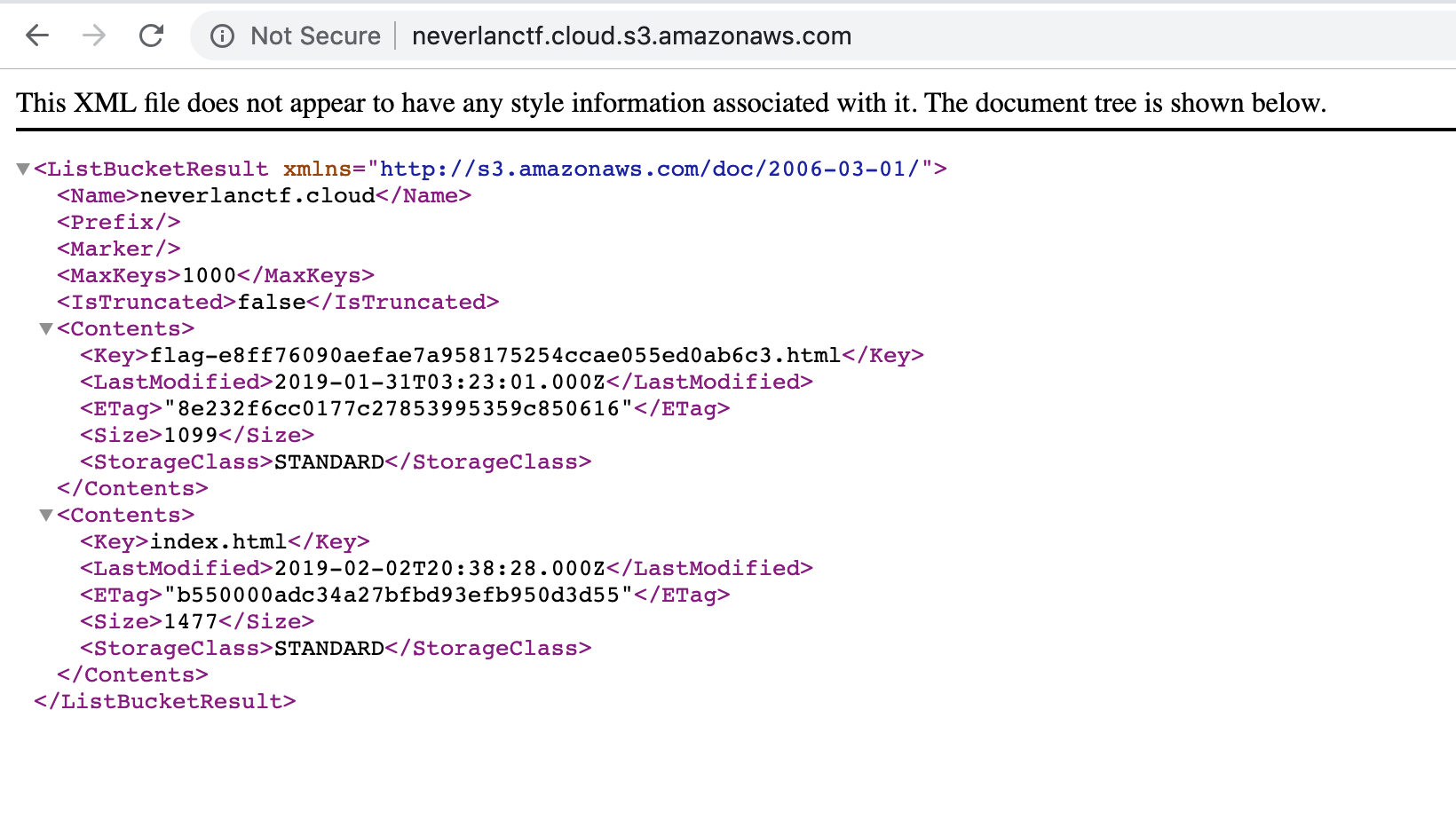
- SubDomain enumeration of a AWS cloud at
neverlanctf.cloud. Particularly mentioned that subdomain enumeration tools wont work…
Ans: flag-e8ff76090aefae7a958175254ccae055ed0ab6c3.html at http://neverlanctf.cloud.s3.amazonaws.com/ –>
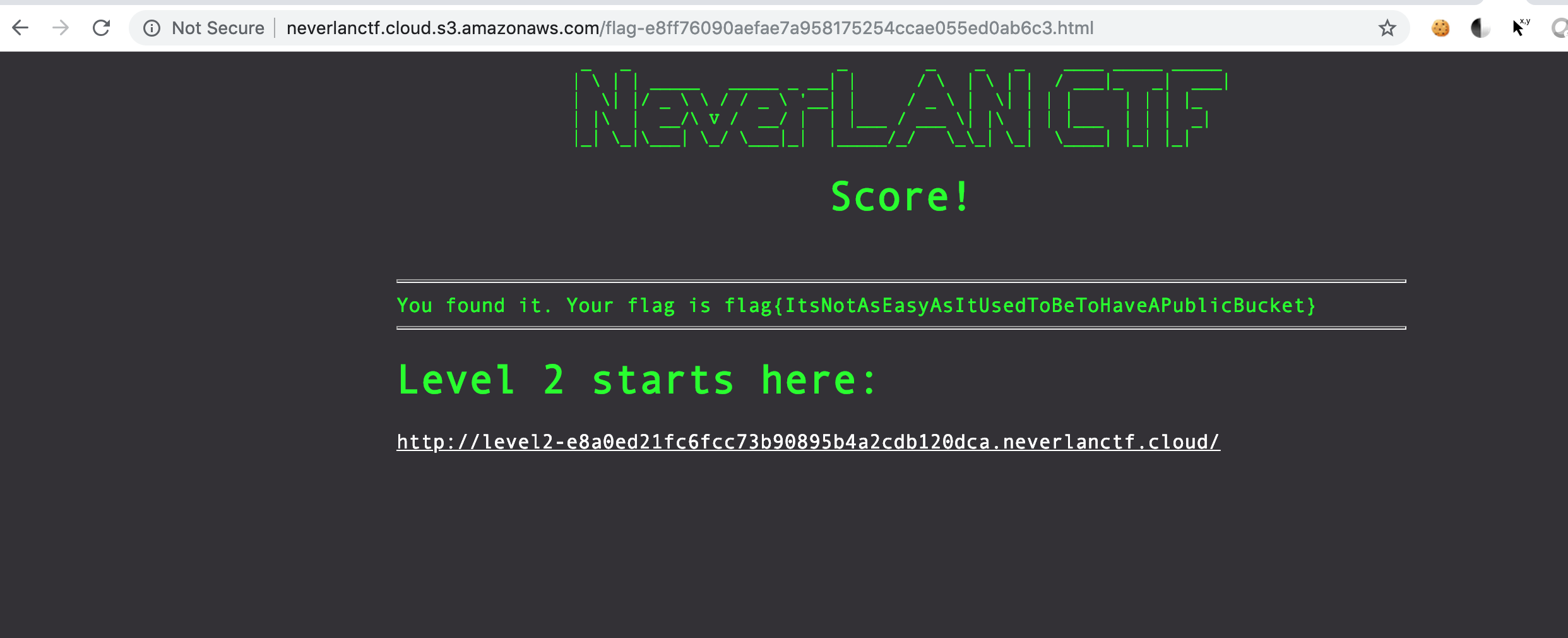
Thoughts:
The Cloud Capture the flag:
* Level1 —> SubDomain Enumeration (Given a website hosted from GCP or AWS, Find all subdomains —> they assured there is no xss, csrf or anything else…)
* The page has a comment not to shortcut using `Sublist3r - A subdomain enumeration tool` and that it won’t help us
* Recon for the cloud:
* Read through the source code
* Read through the content
* Possible subdomains already listed somewhere?
* Checked an error page —> we get a key and some details in the error page. The error has a key which is base64 encoded and decoding that is also garbage….
* Could we leverage the error page to find the cloud provider?
* The error 404 said there was no error.html so it return NoSuchKey
* Ok, google for the error returns AWS S3 Bucket
* Research how AWS S3 handles the subdomains or configures them…
* Searching for /robots.txt threw this issue
* Robots.txt ensure they are now seen by web crawlers
* http://neverlanctf.s3.amazonaws.com
* Providing a s3 type url throws —> access denied
* AWS S3 Recon:
* AWS S3 domains names == bucket names
* Its is unique and has a global scope
* Each subdomains has a separate s3 bucket for it with the same name
* Subdomains have its own s3 buckets with exact names as subdomains.
* The level hints that using subdomain enumeration tools won’t be a success like sublist3r
NMAP Scan:
root@kali:~/Desktop/KeyZ# nmap -sS -A neverlanctf.cloud
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-03 13:59 PST
Stats: 0:00:18 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 32.26% done; ETC: 13:59 (0:00:00 remaining)
Nmap scan report for neverlanctf.cloud (52.218.192.219)
Host is up (0.047s latency).
rDNS record for 52.218.192.219: s3-website-us-west-2.amazonaws.com
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Amazon S3 httpd
|_http-server-header: AmazonS3
|_http-title: NeverLAN CTF.cloud
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: 3Com SuperStack 3 Switch 3870 (95%), OSRAM Lightify ZigBee gateway (93%), Satel ETHM-2 intruder alarm (92%), HP ProCurve 2524 switch or 9100c Digital Sender printer (92%), Apple TV 5.2.1 or 5.3 (91%), Denver Electronics AC-5000W MK2 camera (91%), NEC UNIVERGE SV8100 PBX (88%), Cisco SG 500 switch (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 22 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 4.92 ms 192.168.0.1
2 24.17 ms 142.254.236.153
3 13.16 ms agg62.lsaicaev01h.socal.rr.com (24.30.168.9)
4 19.99 ms agg11.lsaicaev01r.socal.rr.com (72.129.18.192)
5 18.77 ms agg26.lsancarc01r.socal.rr.com (72.129.17.0)
6 17.66 ms bu-ether16.lsancarc0yw-bcr00.tbone.rr.com (66.109.6.102)
7 14.39 ms 0.ae0.pr1.lax00.tbone.rr.com (107.14.17.248)
8 14.41 ms 24.27.236.33
9 ... 13
14 38.49 ms 205.251.232.61
15 ... 21
22 75.63 ms s3-website-us-west-2.amazonaws.com (52.218.192.219)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.55 seconds
Nslookup:
Dig:
* Soa
* Axfr
* dynadot
Whois:
* Used some online subdomain pentest-tools, shodan as well
* It should always be a security misconfiguration or some property of AWS as there must be no obvious bugs in cloud
* Read about amazon s3 bucket subdomains
* Full name:
* http://neverlanctf.cloud.s3-website-us-west-2.amazonaws.com
* An easy scan of www.neverlanctf.cloud has a different 404 error while other subdomains are not reachable
* Also, dnscan results show www as a subdomain and stale dns entries of a lot more which were not useful
* Virtual hosting?
* VH it is
* Tried Virtual hosting?https://docs.aws.amazon.com/AmazonS3/latest/dev/VirtualHosting.html
* Tried s3.amazonaws.com
* http://neverlanctf.cloud.s3.amazonaws.com/
* Got a new asset
* Flagxxxx.html
* Got the level1 flag
* —> flag-e8ff76090aefae7a958175254ccae055ed0ab6c3.html
* List bucket lists
- The Ctf ended before I could complete level2…
Reverse Engineering
Update pending….
References:
- https://pubweb.eng.utah.edu/~nmcdonal/Tutorials/EncryptionResearchReview.pdf
- https://en.wikipedia.org/wiki/Substitution_cipher
- https://en.wikipedia.org/wiki/Polyalphabetic_cipher
- https://www.guballa.de/substitution-solver
- http://www.ancientscripts.com/akkadian.html
- https://crypto.interactive-maths.com/pigpen-cipher.html
- https://interestingengineering.com/11-cryptographic-methods-that-marked-history-from-the-caesar-cipher-to-enigma-code-and-beyond
- https://access.redhat.com/blogs/766093/posts/1976023
- https://docs.aws.amazon.com/AmazonS3/latest/dev/VirtualHosting.html
